PHP is one of the most widely used languages for web application development, but when we talk about security, it is also the most criticized one. PHP security has always been a concern as the language is vulnerable to several attacks such as cross-site scripting (XSS), SQL injection, local file inclusion, and path traversals. This could then cause a web program to execute a file from another location on the system.
PHP coders need to prioritize security and take steps to protect their applications from vulnerabilities. Being aware of security threats and regularly updating to the latest versions are some of the web application security best practices for PHP.
In this post, we will discuss some of the most common security issues PHP developers face and provide solutions to help you keep your applications safe. Without further ado, let’s dive in and learn how to battle the bad guys and implement security measures in PHP web apps.
Protect your PHP Web App with our expert security services
Common Security Vulnerabilities & Protection Measures
Like any technology, PHP is not immune to security vulnerabilities. Let’s discuss common security vulnerabilities in PHP web apps and the measures to keep PHP protected against them.
Also Read: .NET Vs. PHP Vs. Java Vs. Python – Which Language Is Better For Web Development?
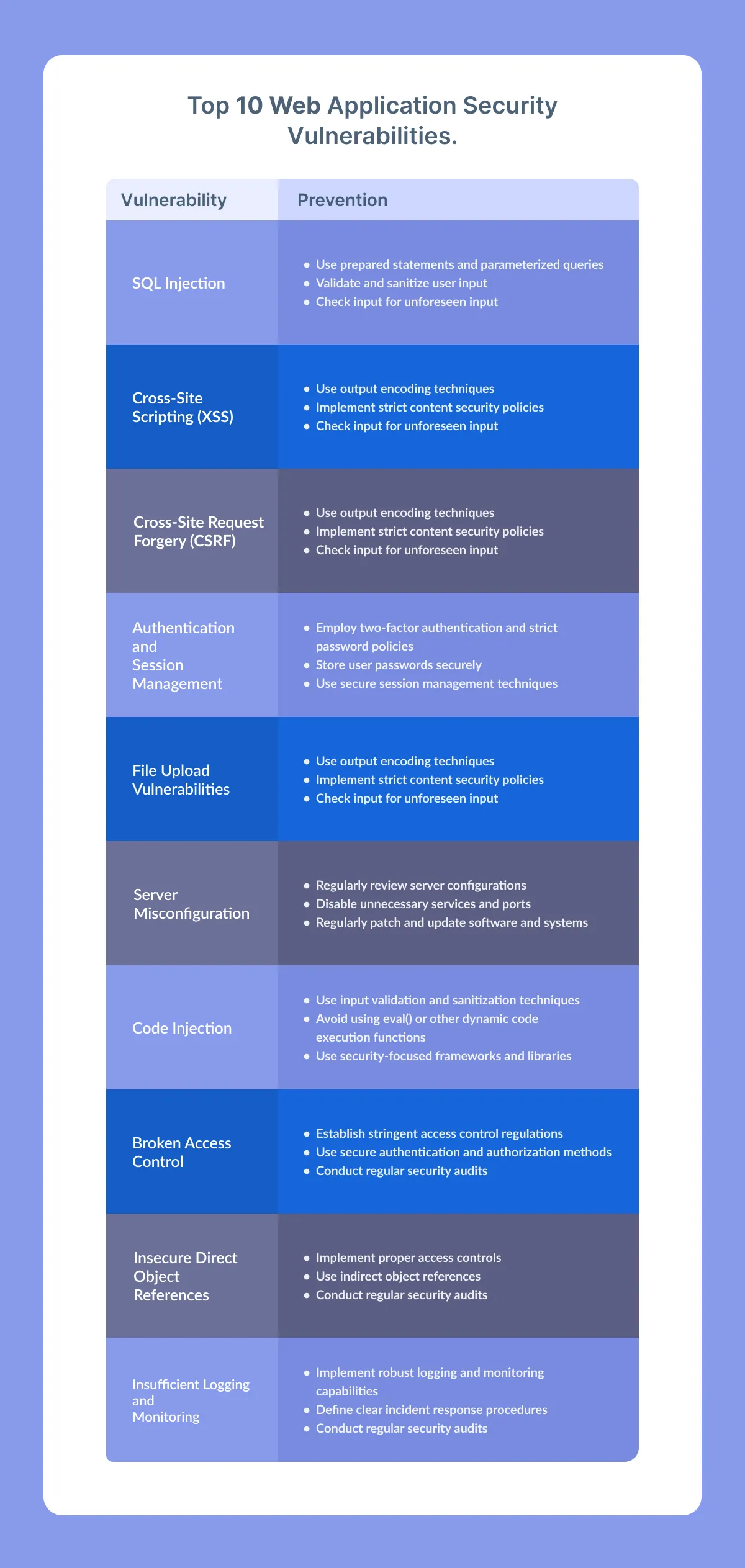
Vulnerability 1: SQL Injection
SQL injection vulnerabilities typically arise in PHP when web applications construct SQL queries by concatenating user-supplied input with SQL commands. For instance, if a malicious user inputs SQL code into one of these fields, the application may execute the code, potentially leading to data theft, system compromise, or other criminal activities.
Protection measures:
- Use prepared statements and parameterized queries instead of dynamic SQL statements to prevent attackers from injecting malicious SQL code.
- When you hire PHP developers, ask them to validate and sanitize user input to ensure that it contains only expected characters and formats.
- Before processing input, use input validation techniques to check for unforeseen input, such as erroneous data types or values.
Vulnerability 2: Cross-Site Scripting (XSS)
Cross-site Scripting (XSS) is a web security vulnerability that allows attackers to inject malicious code into a web page viewed by other users. It happens when an application fails to sanitize user input correctly, allowing the attacker to insert harmful code such as JavaScript, HTML, or other scripting languages. When a victim visits the web page with the injected code, the malicious code can execute and potentially steal sensitive information or hijack the user’s session.
XSS attacks can be particularly dangerous because they can bypass authentication controls, allowing an attacker to access sensitive information without needing a valid login. Web applications written in PHP are commonly targeted for XSS attacks, making it essential to implement proper input sanitization and validation techniques to prevent this type of vulnerability.
Protection measures:
- Use output encoding techniques to prevent attackers from injecting malicious scripts into web pages.
- Ask custom PHP development services provider to implement strict content security policies that prevent scripts from being executed from external sources.
- Before processing input, use techniques for input validation to look for unforeseen input, such as erroneous data types or values.
Protect your PHP Web App with our expert security services
Vulnerability 3: Cross-Site Request Forgery (CSRF)
Cross-site Request Forgery (CSRF) is a security vulnerability. In a CSRF attack, a hacker can trick a user into executing unintended actions on a web application. This can happen when the user visits a malicious website or clicks on a link or button that contains a hidden request to the target application.
If the user is already authenticated to the target application, the attacker can use the session to perform unauthorized actions on the user’s behalf. For example, they can change the user’s password, transfer money from their account, or delete important data.
Protection measures:
- One should implement strict authentication and permission rules to guarantee that only authorized users may access the website and take action there.
- When you hire software developers, ask them to use CSRF tokens to confirm that the user, not an attacker, made the request.
- Use input validation techniques to screen input for unforeseen elements, such as erroneous data types or values, before processing it.
Also Read: Node.Js Vs .NET Vs. PHP: Choosing The Right Stack For Software Development
Vulnerability 4: Authentication and Session Management
Authentication vulnerabilities are weaknesses in the methods used to verify the identity of users, which can allow attackers to gain unauthorized access to sensitive data. For example, an application that does not correctly validate user input during login could be vulnerable to a brute force attack, where an attacker tries many username/password combinations until they find one that works.
Session management vulnerabilities refer to how web applications manage and maintain user sessions. If an attacker can hijack a user’s session, they can impersonate the user and perform actions on their behalf, such as changing their account settings or making unauthorized purchases. It can happen if the application uses predictable session IDs or if the session timeout is too long, among other factors.
Both authentication and session management vulnerabilities are common in PHP applications and can be exploited by attackers to gain unauthorized access or cause other types of harm. Developers need to be aware of these vulnerabilities and implement appropriate security measures to protect against them.
Protection measures:
- Employ two-factor authentication and strict password policies to make sure that only authorized users may access the system.
- Store user passwords securely, using strong encryption techniques and hashing algorithms.
- Use PHP secure session management techniques to prevent session hijackings, such as session timeouts and regeneration of session IDs after each login.
Vulnerability 5: File Upload Vulnerabilities
File upload vulnerabilities are security issues that can occur in web applications, including those built using PHP. These vulnerabilities allow attackers to upload files, such as scripts or malware, to a server by exploiting weaknesses in the application’s file upload functionality.
Once uploaded, one can execute the malicious files on the server, steal sensitive data, or perform other malicious actions. For example, an attacker could upload a PHP file that contains malicious code, which could be executed on the server, giving the attacker control over the affected system.
Protection measures:
- Implement strict file type and size restrictions to prevent users from uploading malicious files.
- Scan uploaded files for viruses and malware using a reputable antivirus software to keep PHP protected against threats.
- Store uploaded files in a separate directory with restricted permissions to prevent unauthorized access and execution.
Also Read: PHP Guide: Vital Things You Should Know About PHP
Vulnerability 6: Server Misconfiguration
Server misconfiguration can create vulnerabilities that attackers can exploit. For example, a server may have weak passwords, incorrect file permissions, or other configuration errors that make it easier for attackers to gain unauthorized access to the system. These misconfigurations occur when a server is not properly set up.
One can exploit these vulnerabilities to steal sensitive data, modify system configurations, or even take complete control of the affected system. Server administrators must ensure their systems are correctly configured to minimize the risk of these attacks.
Protection measures:
- Regularly review server configurations and ensure that they follow PHP security best practices and guidelines.
- Disable unnecessary services and ports to reduce the attack surface.
- Regularly patch and update software and systems to address known vulnerabilities and security issues.
Protect your PHP Web App with our expert security services
Also Read – What’s All Is There In The Store Of WordPress 5.5- Let’s Take A Sneak Peak
Vulnerability 7: Code Injection
Code injection is a common vulnerability in PHP applications that allows attackers to insert and execute malicious code into the application. This can occur when an application fails to properly sanitize user input, such as data entered into a form or URL parameters, before using it to construct dynamic SQL queries, system commands, or other types of code.
Once the attacker successfully injects the malicious code, they can use it to steal sensitive information, take control of the application or server, or perform other malicious activities. Code injection attacks can be particularly dangerous because they can occur without the user’s knowledge and can be challenging to detect.
Protection measures:
- Use input validation and sanitization techniques to ensure user input contains only expected characters and formats.
- To keep PHP secure, avoid using eval() or other dynamic code execution functions.
- Use security-focused frameworks and libraries that protect against code injection attacks.
Vulnerability 8: Broken Access Control
Broken access control vulnerabilities in PHP refer to security weaknesses that can allow attackers to access resources or perform actions that should be restricted. This can happen when the authentication and authorization controls are not adequately implemented.
Attackers can exploit these vulnerabilities to bypass access controls and gain access to confidential information, modify data, or perform other actions that they should not be able to do. For example, suppose a user can access a web application page or functionality without being properly authenticated or authorized. In that case, it can lead to unauthorized access to sensitive data or allow the user to perform malicious actions.
Protection measures:
- Establish stringent access control regulations to ensure that only authorized users can access critical resources.
- Use PHP secure authentication and authorization methods, such as role-based access control (RBAC) and multi-factor authentication, to ensure user identity.
- Conduct regular security audits to identify and address access control vulnerabilities.
Also Read: MEAN Stack Vs. PHP Vs .Net: What’s The Best Choice For You?
Vulnerability 9: Insecure Direct Object References
An insecure direct object reference is a vulnerability that arises when a web application doesn’t correctly validate user input or enforce access controls while accessing internal objects such as files or database records. Due to this vulnerability, attackers may manipulate or tamper with the parameters of a request to access unauthorized resources or data.
For instance, if an application uses sequential numbering to identify files, an attacker can manipulate the number in the request and access a file they shouldn’t have access to. This can result in the disclosure of confidential information or unauthorized access to critical resources.
Protection measures:
- Implement proper access controls to limit access to internal objects only to authorized users.
- Use indirect object references that map internal objects to public references, ensuring one cannot access internal objects directly.
- Conduct regular PHP security audits to identify and address insecure direct object reference vulnerabilities.
Also Read – Top 15 Best Databases for Web Applications To Use In 2025
Vulnerability 10: Insufficient Logging and Monitoring
Insufficient logging and monitoring is a security vulnerability in PHP applications when proper logging and monitoring mechanisms are lacking. This means the application fails to record important events or activities, and there is no way to detect security incidents or malicious activity.
Attackers can exploit this weakness by performing actions that are not logged or monitored, allowing them to evade detection and continue their attacks. For example, an attacker could use a vulnerability in the application to steal sensitive data, and the lack of logging and monitoring could prevent the attack from being detected.
Proper logging and monitoring mechanisms are essential for detecting and responding to security incidents. By monitoring the activity and events within an application, security teams can quickly identify and respond to threats, preventing further damage to the system or compromise of sensitive information.
Protection measures:
- Implement robust logging and monitoring capabilities to detect and alert on suspicious activities and security incidents.
- Define clear incident response procedures and train personnel on how to respond to security incidents.
- Conduct regular PHP security audits to identify and address insufficient logging and monitoring vulnerabilities.
Custom PHP development services significantly enhance the security posture of their PHP web applications and defend themselves from possible attackers by resolving these vulnerabilities and putting the recommended safety precautions into practice. Developers should often assess and upgrade their security procedures to keep their applications safe.
Protect your PHP Web App with our expert security services
Best Practices for Secure PHP Web App Development
PHP web application security demands a proactive, all-encompassing strategy that tackles possible vulnerabilities from the beginning. PHP security best practices should be created and maintained using the following:
Regular Updates and Patches
Frequent upgrades and patches must maintain the security and integrity of PHP web applications. Although older versions of PHP and other dependencies can include known vulnerabilities, developers should ensure they build their applications on the most recent versions of such components. Developers should also often evaluate and implement security fixes to reduce possible vulnerabilities.
Code Reviews and Penetration Testing
The best way to find and fix possible PHP security flaws in web applications is through code reviews and penetration testing. A code review can help developers find security problems early in the development process so they can fix them before the program goes online. On the other side, penetration testing entails simulating assaults on the program to find potential weaknesses that attackers may use.
Secure Configuration and Server Hardening
The security of a PHP web application must be maintained by adequately setting the server and protecting it from potential attacks. It also entails putting in place safe server setups with firewalls, intrusion detection systems, and SSL encryption. In addition, developers should periodically check their servers for possible vulnerabilities and apply PHP security fixes as necessary.
Educating Developers and Users on Security Best Practices
To help prevent possible security dangers, one must train developers and users on PHP security best practices. Developers should adhere to secure coding best practices, frameworks, and tools. Users should be instructed on the proper use of passwords and given the go-ahead to create secure passwords, turn on multi-factor authentication, and keep their login information private.
Input Validation and Sanitization
Developers should always validate and sanitize user input to ensure it meets the expected criteria and prevent attackers from injecting malicious code. They can do this by:
- using server-side validation and sanitization libraries
- using built-in PHP functions such as `filter_var()` and `htmlspecialchars()`.
Least Privilege Principle
The least privilege principle involves providing users and applications with the minimum level of access necessary to perform their tasks. This lowers the potential attack surface and decreases the harm a PHP security breach may inflict. Users should only have the rights they need to do their duties, and developers should make sure their programs adhere to the concept of least privilege.
Secure Password Storage
Storing passwords securely is critical for protecting user data. Developers should use strong encryption algorithms and hashing functions such as bcrypt or Argon2 to store passwords. Additionally, developers should never store passwords in plaintext and avoid using common passwords or easily guessable passwords.
Access Control and Authentication
Proper access control and authentication mechanisms are crucial for maintaining PHP security for web applications. Developers should ensure that users are authenticated before accessing sensitive data or performing critical actions. Additionally, developers should implement role-based access control to limit user access to specific features or resources.
Use of Security Frameworks and Libraries
Developers should think about utilizing security frameworks and libraries that are tried and trusted for being secure. These frameworks and libraries can offer extra security features and functionalities including encryption, secure session management, and user authentication and authorization.
Why Choose ValueCoders For Secure PHP Web App Development?
ValueCoders is a well-established software development company providing secure PHP web app development services to clients worldwide for over 18 years. The following are some reasons for selecting ValueCoders for your secure PHP web app development requirements:
Also Read: Top 21 PHP Web App Development Companies
Experienced PHP developers
ValueCoders has a team of skilled PHP developers having expertise in various PHP frameworks, including CodeIgniter, Laravel, Yii, and Symfony. They are experts in creating social networking sites, e-commerce websites, and specialized online apps. Therefore, whatever the requirements are, you can hire dedicated software development teams to implement needed changes.
Security measures
Each web application must consider security carefully. By adhering to industry best practices and utilizing cutting-edge security tools and technologies, ValueCoders makes sure that your web application is as secure as possible.
Customized solutions
ValueCoders offers specialized PHP web app development services catered to your company’s unique needs. To understand their clients’ business needs and offer specialized solutions, they collaborate closely with them.
Agile development methodology
ValueCoders follows an agile development methodology that allows for flexibility and faster delivery of projects. They prioritize client satisfaction and provide regular updates on the project’s progress.
Cost-effective
ValueCoders offers cost-effective PHP secure web app development services without compromising on quality. They have flexible pricing models and provide transparent billing to clients.
Conclusion
PHP is still a popular language for creating online applications, but it can also leave web programs vulnerable to several security flaws. Therefore, developers should follow the PHP security checklist and adhere to PHP web application security best practices to build a safe and robust application.