In this interconnected digital world, where the internet has become an integral part of our lives, the need for robust website security against cyber threats has never been more pressing.
Data breaches and cyber-attacks dominate the headlines in today’s time. They cost businesses an avg. of $4.35 billion in 2022. Therefore, safeguarding your website is not just a luxury but an absolute necessity.
This blog post will unravel the complexities of web security, empowering you with the knowledge and strategies to protect your online presence from hackers and malware.
Cyber Web Threats Stats
-
-
- As per a report by DWG, approx. 50K websites are hacked daily, and there is an attack on a website every 40 seconds.
- According to a website security report by Amazon, 18% of websites have severe critical threats, and about 4.1M websites contain malware simultaneously, among which eCommerce websites are most vulnerable to these threats.
- Approx. 97% of security breaches exploit WP plugins, as reported by Hostinger.
- A report by Salt Labs shows that 34% of organizations contain no API security.
-
Understanding Cyber Threats
Cyber threats refer to the potential for malicious activities carried out over the internet or other networks that aim to damage, disrupt, or gain unauthorized access to personal data, networks, or computer systems.
The impact of cyber threats on websites can be devastating. It leads to the loss of sensitive data, such as:
- Customer information
- Financial records
- Intellectual property
- Disrupt website operations
Ultimately, it leads to website downtime, resulting in lost revenue & customer trust. In most severe cases, cyber threats can even lead to the complete shutdown of a website.
The motivations behind cyber attacks are varied & can range from financial gain to data theft, espionage, and even political motivations.
- Financial gain is the primary motivation. In this, cybercriminals steal sensitive data to sell on the dark web or hold data hostage through ransomware attacks.
- Data theft is another common motivation, with attackers seeking to steal personal or proprietary information for various purposes.
However, in some cases, cyber attacks are carried out for ideological reasons or to cause disruption and chaos.
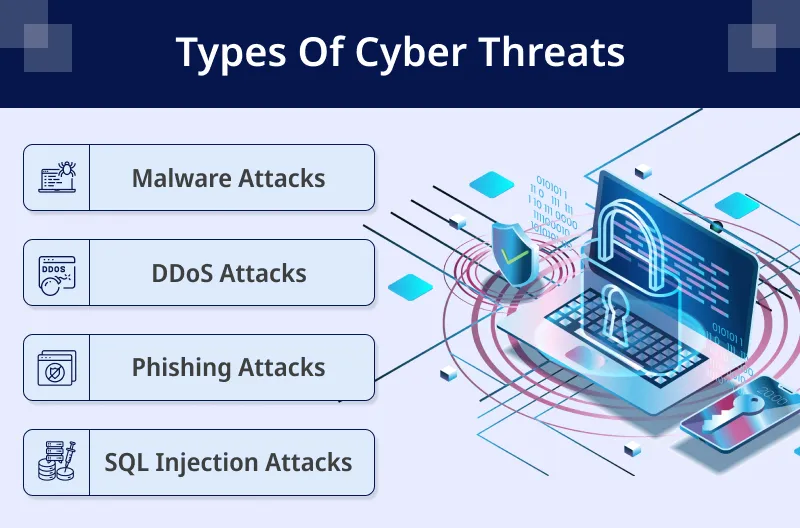
Common Types of Cyber Threats
The United Kingdom had the highest number of cybercrime victims per million internet users in 2022. The United States of America had the second-highest number of victims in the same year.
You can significantly reduce the likelihood of falling victim to these attacks by being aware of various cyber threats. So, stay vigilant, informed, and, most importantly, secure.
Also Read: Choose The Right Web Development Technology For Your Project
Let’s have a quick look at the common types of cyber threats:
Malware Attacks
Malware (short for malicious software) is typically designed to infiltrate & damage computers without the users’ consent. It includes:
- Viruses
- Worms
- Trojans
- Ransomware
- Spyware
Malware can steal, delete, or encrypt data, alter or hijack core computing functions, and monitor users’ computer activity without permission.
DDoS Attacks
Distributed Denial of Service (DDoS) attacks aim to develop a website or a network resource that is not available to its intended users by overwhelming it with mere internet traffic. This leads to significant downtime & loss of business.
Phishing Attacks
Phishing is a method used by cybercriminals to trick individuals into revealing sensitive information, such as credit card details, usernames, and passwords. It is done by pretending to be a trustworthy entity in electronic communication.
SQL Injection Attacks
SQL injection is termed as a code injection technique that attackers use to exploit vulnerabilities in a website’s database. The attacker manipulates the site’s SQL queries to attain unauthorized access to sensitive data or even execute administrative operations on the database.
Implement robust security measures.
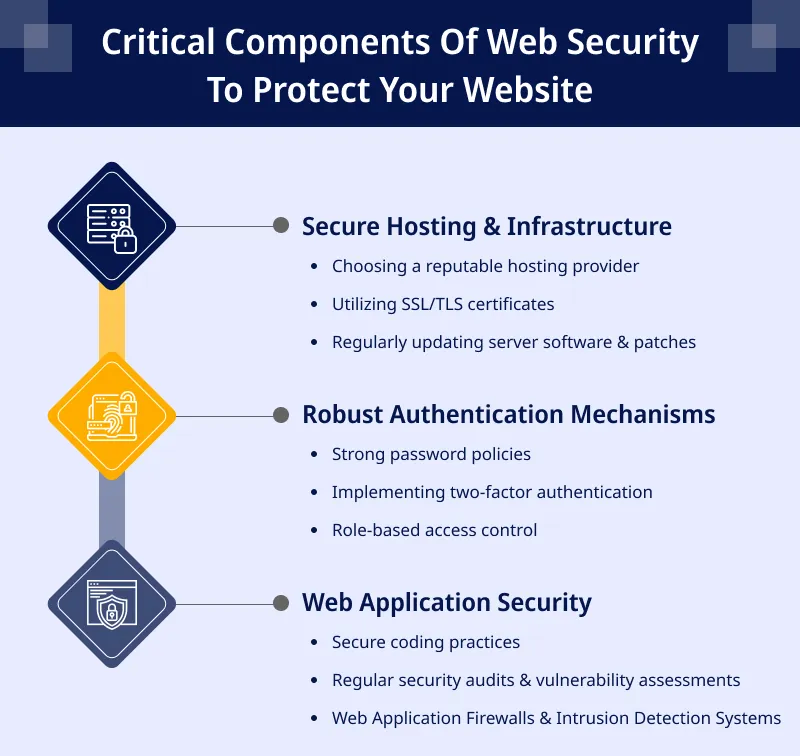
Key Components of Web Security
Website security against cyber threats is a critical aspect of maintaining a safe & trustworthy online presence. It is a multifaceted discipline that requires a comprehensive approach.
Hence, it is essential to understand the critical components of web security to protect your website from cyber threats.
Secure Hosting & Infrastructure
Choosing a reputable hosting provider
A reliable hosting provider will have robust security measures to protect your website from various threats. Look for providers that offer features such as:
- Firewalls
- Intrusion detection systems
- Regular security updates
Utilizing SSL/TLS certificates
These certificates encrypt the data transmitted between your website and its users, ensuring that sensitive information remains confidential. You create a secure connection and protect your users’ data from interception by implementing SSL/TLS.
Regularly updating server software & patches.
Outdated software can have vulnerabilities that hackers can exploit. You can close these vulnerabilities and minimize the risk of unauthorized access by staying updated with these latest security patches.
Robust Authentication Mechanisms
Strong password policies
Authentication is vital to web security. Implementing strong password policies is the first line of defense against unauthorized access. Create complex passwords that combine letters, numbers, and special characters.
Additionally, enforce password expiration and account lockout policies to prevent brute-force attacks.
Implementing two-factor authentication
With 2FA, users must provide a second form of verification, such as a unique code sent to their smartphones, in addition to the password. This reduces the risk of unauthorized access, even if passwords are compromised.
Role-based access control
RBAC is another effective mechanism for web security. RBAC ensures that users are granted access only to the resources and functionalities necessary for their roles. Limiting access privileges minimizes the potential damage that compromised accounts can cause.
Web Application Security
Secure coding practices
It focuses on protecting the code and functionality of your website. It prevents common vulnerabilities like cross-site scripting (XSS) and SQL injection attacks.
To mitigate these risks, developers should follow the best approaches, such as output encoding, input validation, and parameterized queries.
Regular security audits & vulnerability assessments
The above is essential to identify and address any weaknesses in your web application. Security professionals specializing in identifying potential vulnerabilities and recommending appropriate remediation measures do these assessments.
Web Application Firewalls & Intrusion Detection Systems
WAF & IDS provide additional protection against attacks.
A WAF filters and monitors incoming web traffic, blocking malicious requests and protecting against common web application attacks.
IDS, on the other hand, detects and alerts administrators about possible intrusion attempts, allowing for timely response and mitigation.
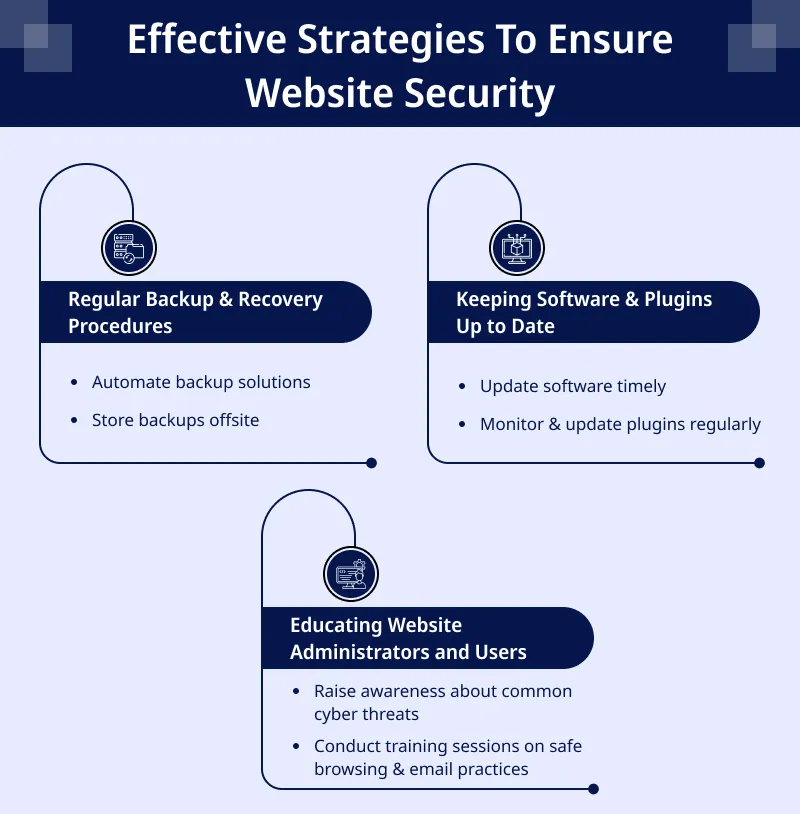
Best Practices for Web Security
With the increasing number of cyber threats, adopting best practices for website security against cyber threats and its users has become crucial.
Here are some of the most effective strategies to ensure your website’s security.
Regular Backup & Recovery Procedures
Automate backup solutions
Automated backup solutions are a must-have for any website. These solutions automatically back up your website’s data at regular intervals. They also ensure that you have a recent copy of your data in case of unforeseen incidents.
Store backups offsite
Having a backup is not enough. It is equally important to store in secure environments.
Offsite storage protects your data from physical threats like natural disasters or theft. Secure environments, on the other hand, protect your data from cyber threats.
By combining both, you can ensure that your data is safe & can be recovered quickly in case of any disaster.
Also Read: .NET vs. PHP vs. Java vs. Python – Which Language is Better for Web Development?
Keeping Software & Plugins Up to Date
Update software timely
Outdated software can have vulnerabilities that cybercriminals can exploit to gain unauthorized access to your website. Therefore, regularly updating your software to patch any potential security holes is essential.
Monitor & update plugins regularly
Plugins can pose a security risk if not updated regularly. They often have access to sensitive data and can be a potential entry point for hackers. Regular monitoring and updating of plugins help prevent this.
Educating Website Administrators and Users
Raise awareness about common cyber threats
Administrators should be aware of common cyber threats and how to mitigate them. This includes identifying phishing attempts, using secure passwords, and safely browsing the internet.
Conduct training sessions on safe browsing & email practices
Users, on the other hand, should be educated about safe browsing and email practices. This includes:
- Not clicking on suspicious links
- Not downloading attachments from unknown sources
- Using strong, unique passwords for their accounts
Discover our expert web security solutions.
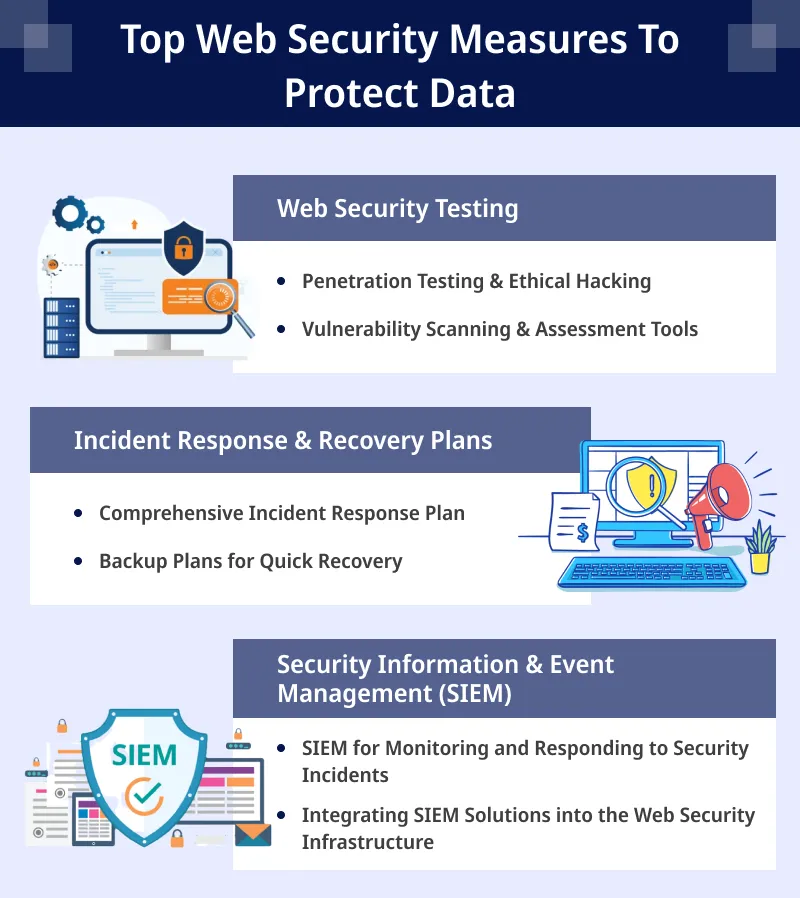
Advanced Web Security Measures
Advanced web security measures are essential to protect sensitive information and also maintain the integrity of your business’s online presence.
By adopting a proactive approach to web security, you can protect your business website from all types of cyber threats and ensure the continuity of your online operations.
Web Security Testing
Penetration Testing & Ethical Hacking
Penetration testing (ethical hacking) is a proactive approach to web security. It involves authorized attempts to breach the website’s security against cyber threats to identify vulnerabilities that malicious hackers could exploit.
By simulating cyber-attacks, organizations can identify weak points in their security infrastructure and take corrective action before a real threat occurs.
Vulnerability Scanning & Assessment Tools
Vulnerability scanning & assessment is another crucial aspect of web security testing. It involves using automated software to scan a system for known vulnerabilities.
Assessment tools then analyze these vulnerabilities, prioritizing them based on severity and providing recommendations for remediation.
Regular vulnerability scanning can help ensure that your website’s security against cyber threats is always up-to-date and capable of defending against the latest threats.
Incident Response & Recovery Plans
Comprehensive Incident Response Plan
An incident response plan is a detailed course designed to handle and manage a security breach or attack.
It outlines the roles & responsibilities of individuals during website security against cyber threats, the procedures for identifying and containing the threat, and the steps to be taken for recovery.
A well-structured incident response plan can significantly reduce the damage caused by a security breach and speed up recovery.
Backup Plans for Quick Recovery
Backup plans are an integral part of any incident response and recovery strategy. Regularly backing up data ensures that critical information can be quickly restored during a breach or data loss.
This not only minimizes downtime but also helps maintain business continuity.
Security Information & Event Management (SIEM)
SIEM for Monitoring and Responding to Security Incidents
SIEM solutions provide real-time analysis of security alerts generated by network hardware & web application development in India. They collect and aggregate log data to identify patterns or anomalies indicating a security incident.
SIEM tools enable quick detection, analysis, and response to potential threats by providing a centralized view of an organization’s security landscape.
Integrating SIEM Solutions into the Web Security Infrastructure
Integrating SIEM solutions enhances your ability to detect and respond to cyber threats. It provides a holistic view of your security posture, allowing for more effective threat management.
Moreover, SIEM integration can help meet compliance requirements by providing comprehensive reporting and audit trails.
Also Read: Building a Dream Team: How to Hire Top iOS, Android, and Web Developers
Top Emerging Trends In Web Security
As technology evolves, so do the threats that target web security. Staying ahead of cybercriminals requires adapting to emerging trends and adopting proactive measures.
Integrating AI and ML technologies can enhance threat detection and response capabilities while prioritizing mobile device security ensures the safety of your users’ data.
Let’s explore them below:
Artificial Intelligence & Machine Learning
Utilizing AI/ML for Threat Detection & Mitigation
Organizations can analyze vast amounts of data and identify patterns that indicate potential threats by leveraging AI & ML algorithms. These technologies have the following benefits:
- Enable the automation of threat detection & response.
- Significantly reduce the time it takes to identify & mitigate security breaches.
- Enhance the accuracy of security systems.
- Continuously learn from new data & adapt to evolving threats.
Potential Challenges & Ethical Considerations
While AI/ML offers immense potential for improving web security, they also present challenges and ethical considerations.
- One challenge is the potential for false positives or negatives where legitimate activities are flagged as threats or actual threats go undetected.
- Striking the right balance between security and user experience is crucial.
- Ethical considerations arise when AI/ML algorithms make decisions that impact user privacy or discriminate against specific individuals or groups.
Mobile Device Security
Addressing the Unique Security Concerns
Mobile websites and apps face unique security concerns, such as:
- Device theft
- Unsecured Wi-Fi networks
- Malicious apps
Hence, organizations must address these concerns to protect sensitive data and maintain user trust.
Mobile-specific Security Measures
Organizations should implement mobile-specific security measures and best practices to enhance mobile device security. These include:
- Secure coding practices
- Encryption of data in transit and at rest
- Two-factor authentication
- Regular security updates
Additionally, educating users about mobile security risks and promoting safe browsing habits can significantly reduce the likelihood of successful attacks.
We handle all your web security needs.
Conclusion
So far, we have seen that cyber threats are constantly evolving, and businesses (from small to big enterprises) must stay one step ahead. By adopting a multi-layered approach, you can safeguard your website from cyber threats.
Moreover, you can fortify your website against potential attacks by taking & implementing advanced web security measures, staying updated with emerging trends, and prioritizing proactive website security against cyber threats practices.
Always remember web security is an ongoing process, and staying vigilant is critical to maintaining a secure online presence.You may also contact a reliable web app development company like ValueCoders, whose web experts help in shielding websites from potential attacks. Hire web app developers from us to ensure the safety of your data and users. Contact us today!