Do you know?
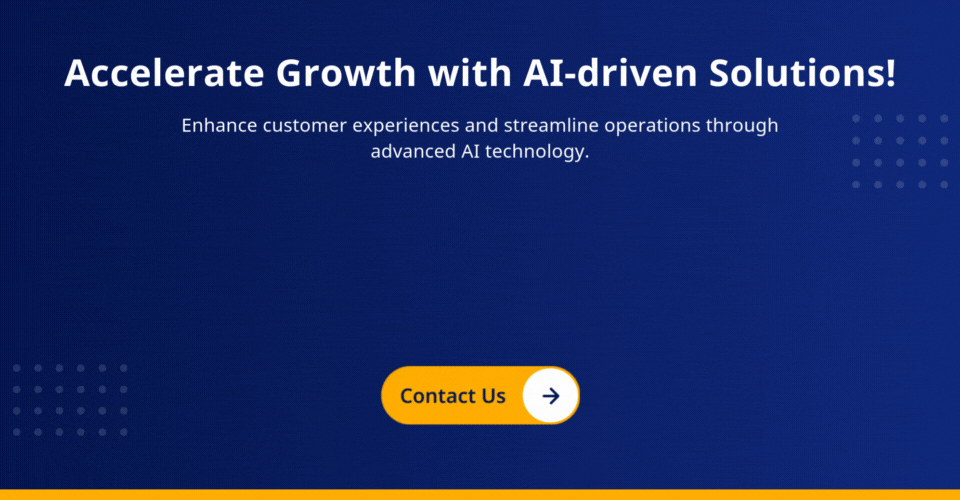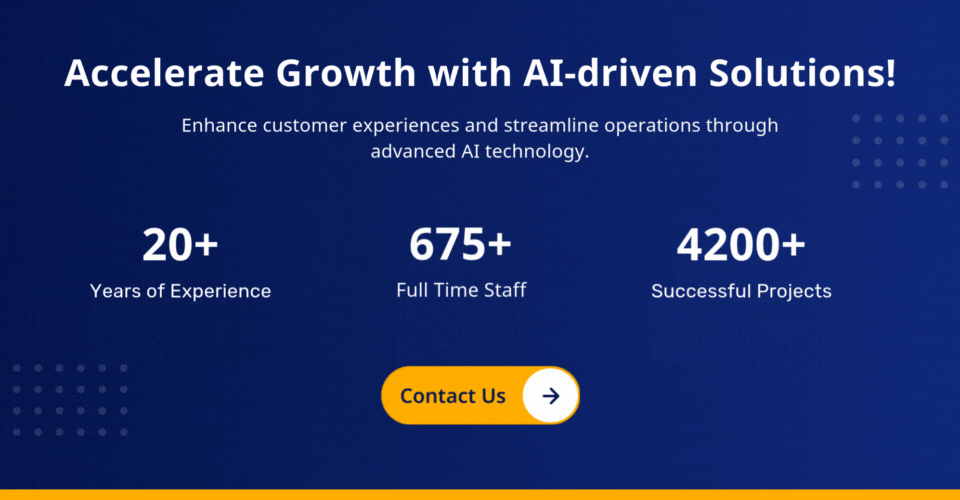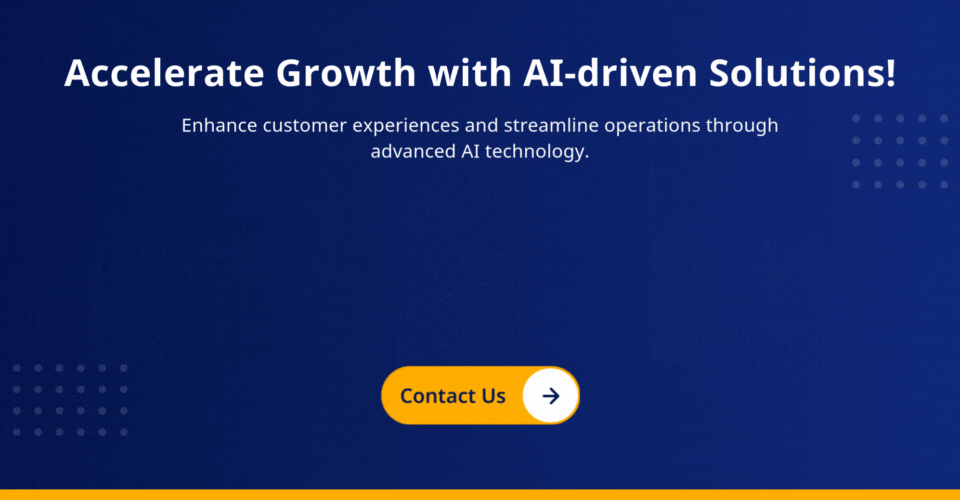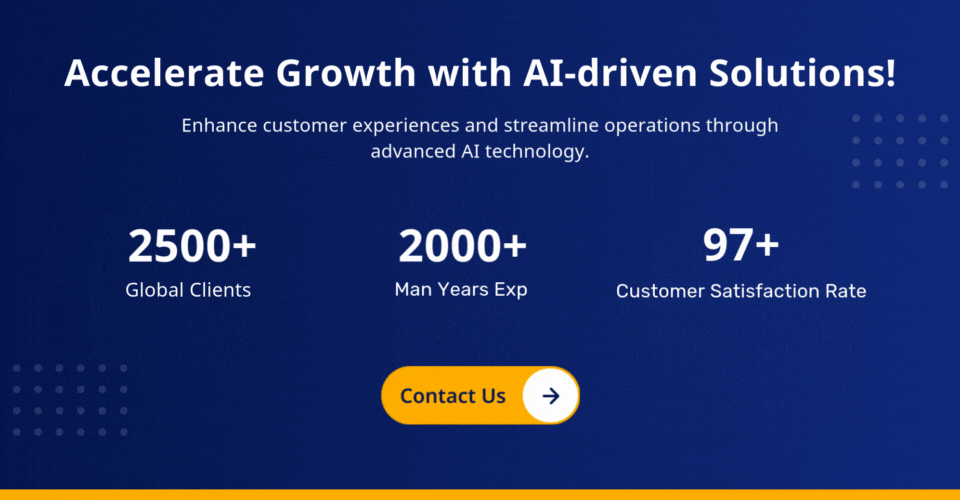
- The global cybercrime damage is going to reach 10.5$ trillion by 2025.
- The world will need to secure approx. 330 bn new software code lines in the year 2025.
- The cyber insurance market will hit 14.8$ trillion by 2025, according to the same source.
In this digital era of modern businesses, cyber threats are spreading at an alarming rate. It has already risen by over 400% in recent years. In fact, global cybersecurity spending is going to exceed $1.75 trillion cumulatively.
Hence, traditional security measures are no longer sufficient to protect sensitive data & systems.
This is why advanced threat detection has become the need of today’s hour. It is an evolved approach that uses modern tools/technologies to identify & neutralize potential threats before they cause major damages.
This detailed guide discusses how advanced threat detection strengthens cybersecurity via five powerful ways of defending & protecting valuable data in an increasingly digital business world.
An Overview of Advanced Threat Detection
Advanced threat detection helps in identifying & mitigating more risky cyber threats in the cybersecurity domain. This technology uses techniques/tools to protect against potential breaches.
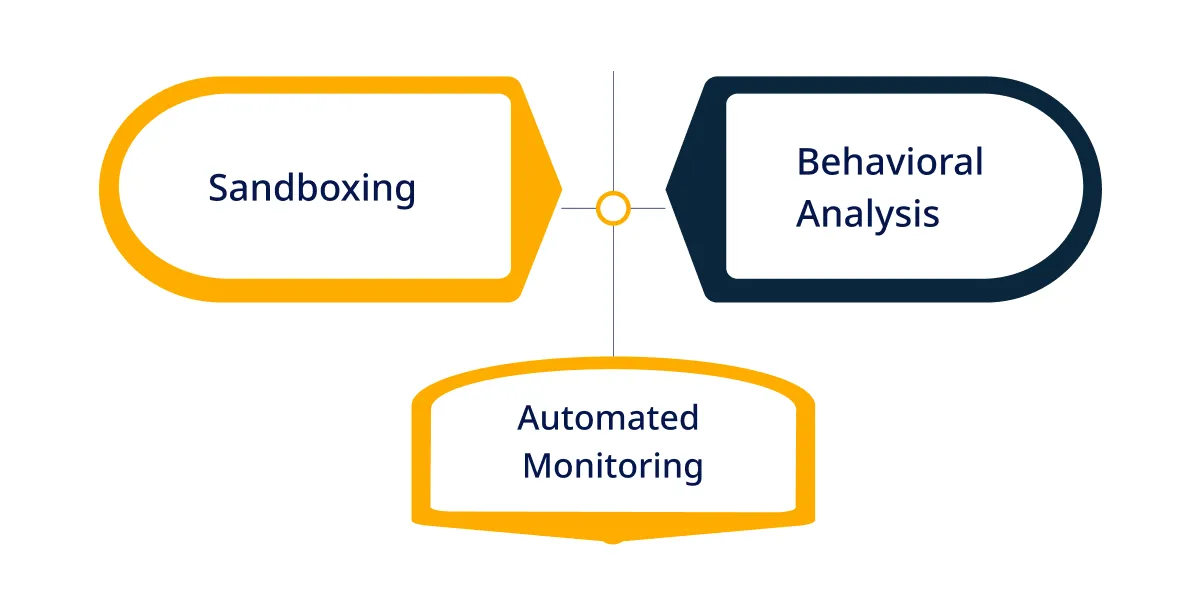
Here, we have listed some core components of advanced threat detection and how they work to increase security:
-
Sandboxing
Sandboxing is a security approach that isolates suspicious files/programs in a controlled environment separate from the leading digital network. This allows security teams to safely analyze the behavior of potentially harmful code without affecting system integrity.
By running the code in a virtual space, sandboxing can detect and neutralize threats before they penetrate the network, ensuring that only safe, endpoint protection and verified files are allowed through.
Experience the future of cybersecurity with advanced threat detection.
-
Behavioral Analysis
This approach involves monitoring & analyzing the behavior of users, network traffic, and systems to identify anomalies that mostly indicate a security threat.
Unlike traditional signature-based threat detection methods, which rely on various known threat patterns, behavioral analysis detects new/unknown threats by recognizing unusual patterns/activities.
This proactive approach enables the identification of sophisticated attacks like zero-day exploits that might evade conventional detection methods.
-
Automated Monitoring
This approach continuously scans the network to identify any sign of malicious activity. These systems use AI/ML algorithms to analyze data in real time, identify trends, and identify patterns that indicate a threat. When paired with top CSPM solutions, they can also proactively identify misconfigurations and compliance gaps across multi-cloud environments.
Organizations respond to potential security incidents more quickly & efficiently by automating the detection process. They actually minimize the impact of any breach. Automated monitoring also helps in reducing the workload on dedicated software teams. Hence, it allows them to focus on more strategic tasks.
Embedding the above-discussed advanced threat detection techniques into cybersecurity solutions can significantly boost a company’s defenses. Hence, businesses can avoid evolving threats and protect their critical assets from any type of cyber attack.
Also read: A Guide To Security In Software Development – White Paper
Types of Advanced Threat Detection Solutions
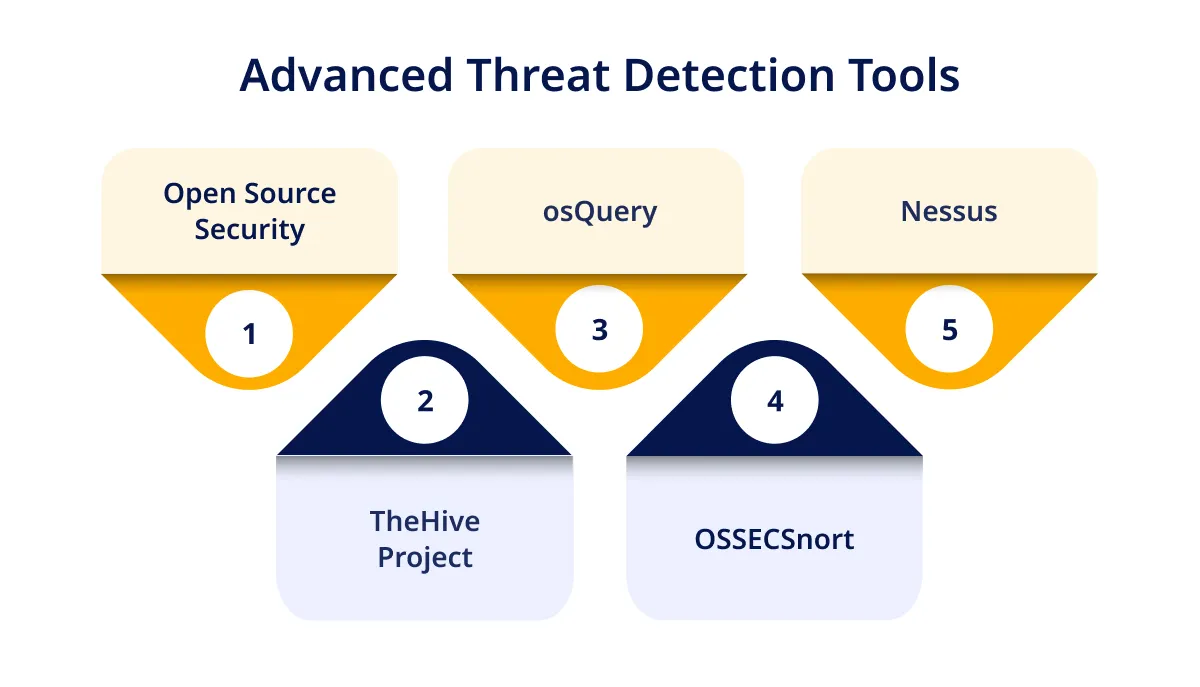
The following tools/technologies are essential for identifying & mitigating potential threats before they cause any significant damage. Have a look at some of the most influential open-source threat detection solutions available in the market:
1. Open Source Security: OSSEC is a scalable, comprehensive, and flexible open-source host-based intrusion detection system. It monitors & analyzes activities on various systems viz. log analysis, Windows registry monitoring, integrity checking, etc.
2. TheHive Project: It is an open-source incident response platform designed to help cybersecurity professionals collaborate & manage security incidents efficiently. It integrates seamlessly with different threat detection tools and provides a powerful interface.
3. osQuery: It is an operating system instrumentation framework that allows users to query all types of aspects of their operating systems using SQL-based queries. Developed by Facebook, it provides detailed insights into system configuration and status.
4. OSSECSnort: It is a widely used open-source network intrusion detection and prevention system. It analyzes network traffic in real-time to find potential security threats based on a comprehensive set of rules.
5. Nessus: Although not entirely open-source, it offers a free version with extensive vulnerability assessment solutions. It scans systems for vulnerabilities that attackers could exploit & provides detailed reports.
Top 5 Ways Advanced Threat Detection Strengthening Cybersecurity
Have a look at the top ways or website security checklists that advanced threat detection use for reliable cybersecurity and building secure applications:
1) Proactive Threat Identification
Proactive threat identification involves detecting potential security threats before they can exploit vulnerabilities or cause harm. It allows organizations to address threats early & prevent significant damage, thus offering perfect risk management in software development.
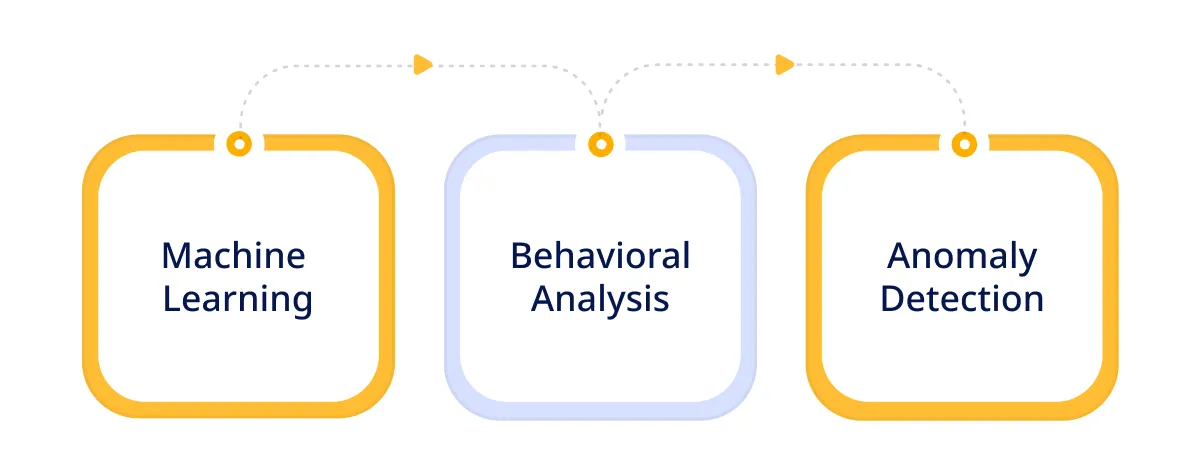
Techniques Used
There are various advanced threat detection leverages several sophisticated techniques:
- Machine Learning: ML algorithms analyze large data to identify patterns & predict potential threats.
- Behavioral Analysis: Monitoring user & system behavior to detect any type of anomaly that indicates malicious activity.
- Anomaly Detection: Identifying deviations from standard patterns that could signify a security threat.
Benefits
These techniques collectively enhance cybersecurity in software development by:
- Identifying threats in their early stages. It further allows for swift action.
- Reducing the window of opportunity for cyber attackers to exploit vulnerabilities.
- Minimizing potential damage & disruption to business operations.
Hence, organizations stay ahead of cyber threats & maintain a robust security posture by incorporating these advanced methods.
Also read: Integrating AI And Machine Learning Into Business Operations
2) Real-Time Monitoring & Response
Real-time monitoring and response have become essential components of a robust cybersecurity strategy. This approach allows organizations to detect & address potential threats as they arise, thus, minimizing damage & maintaining the integrity of their systems.
Continuous Surveillance
Continuous surveillance enables companies to monitor their systems, networks, and data constantly. This proactive approach ensures that any unusual/suspicious activity is identified immediately.
Unlike traditional security information and event management (siem), real-time monitoring provides a dynamic & up-to-the-minute view of the threat landscape. This allows security teams to spot anomalies and potential breaches as soon as they occur.
Immediate Response
Real-time response capabilities are vital for compabies to act swiftly in mitigating threats. When a potential threat is detected, an instant action is taken to contain & neutralize it before it becomes a full-blown security incident. This could involve blocking malicious traffic, isolating affected systems, or deploying patches & updates to vulnerable areas.
Swift response times are a key differentiator in maintaining a resilient cybersecurity posture.The ability to respond quickly not only reduces the threat’s impact but also helps preserve the organization’s reputation & customer trust.
Case Studies
Organizations can effectively counteract threats and safeguard their digital assets by maintaining continuous surveillance & having the capability to act immediately. Several incidents highlight the effectiveness of real-time monitoring & response in preventing breaches:
1. Target Data Breach Prevention
A major retail chain detected unusual network activity through its real-time monitoring systems. The security team acted swiftly to isolate the affected systems & trace the source of the anomaly. This turned out to be an attempted data breach.
By responding immediately, the company was able to prevent the attackers from misusing sensitive customer data. This can save millions in potential losses & reputational damage.
2. Financial Institution Cyber Defense
A leading financial institution safeguards its operations with continuous surveillance and real-time response strategies. When its monitoring systems flagged suspicious login attempts from overseas, the security team quickly intervened.
They implemented additional authentication measures & blocked the suspicious IP addresses. This could have been a significant breach. This prompt action not only protected the institution’s assets but also maintained the confidence of its clients.
3. Healthcare Provider Ransomware Mitigation
A healthcare provider’s real-time monitoring system detected unusual file encryption activity indicative of a ransomware attack. Immediate response protocols were triggered, isolating affected systems and restoring data from backups.
This rapid intervention minimized downtime & ensured that patient care was not disrupted, demonstrating the critical role of real-time response in maintaining operational continuity.
Also Read: Top 10 Web Development Companies Catering to Global Clients
Enhance your protection with cutting-edge threat detection solutions.
3) Enhanced Accuracy with Machine Learning and AI
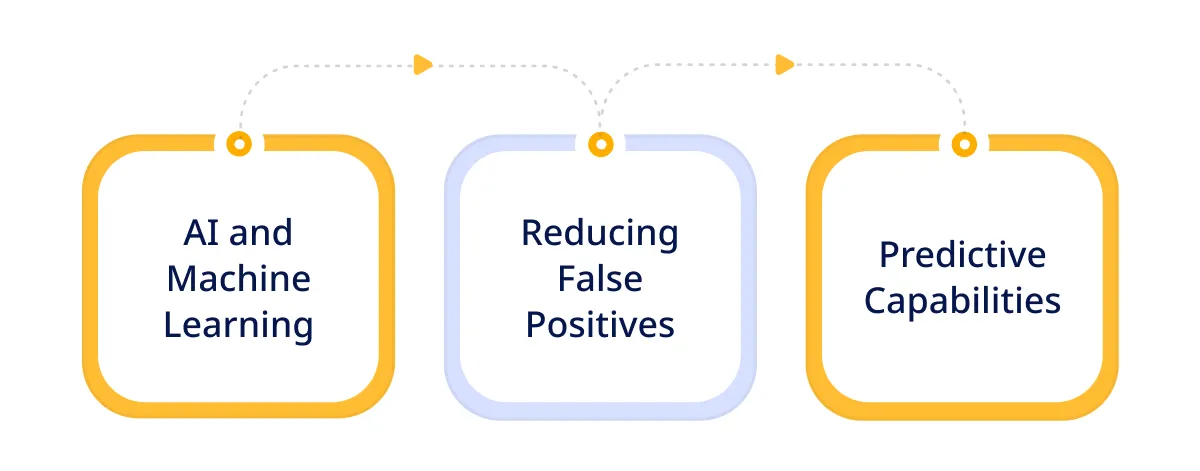
Organizations can achieve higher accuracy in threat detection, reduce the burden of false positives, and proactively defend against future cyber threats by utilizing the power of AI and machine learning.
- AI and Machine Learning: AI/ML have revolutionized threat detection by enabling systems to learn from data and improve over time. These technologies analyze vast amount of information to identify patterns & anomalies that might indicate a security threat.
- Reducing False Positives: Traditional security testing services often generate numerous alerts, many of which are not actual threats. AI/ML algorithms refine the detection process. This ensures that alerts are more accurate, thus saving security teams time & resources.
- Predictive Capabilities: By analyzing trends & historical data, these systems predict future attacks and help organizations prepare defenses in advance. This enhances their overall security posture.
Example:
A leading financial institution implemented an AI-driven threat detection system, significantly improving its ability to detect and respond to threats. Within months, the institution reported a 40% reduction in false positives & a 30% improvement in threat detection accuracy.
4) Comprehensive Threat Intelligence
Advanced threat detection systems use various intelligence sources and malware analysis techniques to understand the threat landscape thoroughly. Let’s know about this below:
Threat intelligence is gathered from various sources, each contributing valuable insights:
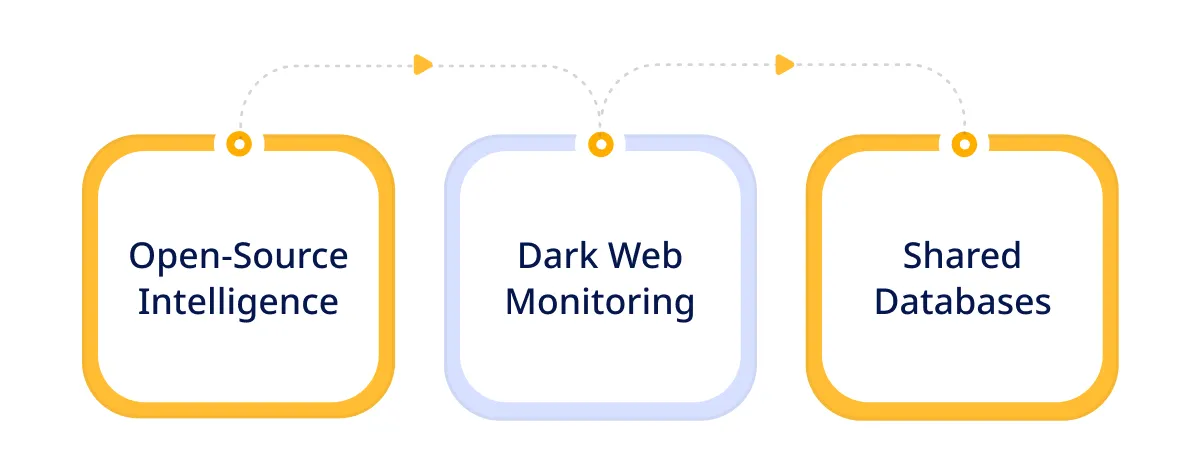
- Open-Source Intelligence: OSINT provide information from publicly available sources viz. websites, social media, and news outlets. It provides valuable context about emerging threats and cybercriminals’ tactics, techniques, and procedures.
- Dark Web Monitoring: The dark web is a hub for illicit activities and a marketplace for stolen data and malware. Monitoring dark web forums and marketplaces can reveal early warning signs of planned attacks or data breaches. This allows organizations to take proactive measures.
- Shared Databases: Platforms like the Cyber Threat Alliance and Information Sharing and Analysis Centers facilitate the exchange of threat information. This helps organizations stay updated on the latest threats and vulnerabilities.
Advanced threat detection systems excel in integrating & analyzing data from many different sources to create comprehensive threat intelligence.
By combining information from OSINT, dark web monitoring, and shared databases, these systems can:
- Detect Emerging Threats: By analyzing data trends and anomalies, advanced systems can identify new threats as they emerge, providing early warnings and enabling proactive defense measures.
- Enhance Threat Context: Integrating diverse data sources provides a richer context for each threat, including the threat actors involved, their motivations, and their methods. This context is crucial for developing effective countermeasures.
- Automate Threat Response: With real-time analysis and integration, advanced systems can automate responses to detected threats, such as blocking malicious IP addresses or isolating compromised systems, thus minimizing the impact of attacks.
5) Automated Threat Mitigation
By integrating automated threat mitigation into their cybersecurity framework, businesses can enhance their ability to swiftly and effectively handle cyber threats. This also ensures a robust defense against evolving cyber challenges.
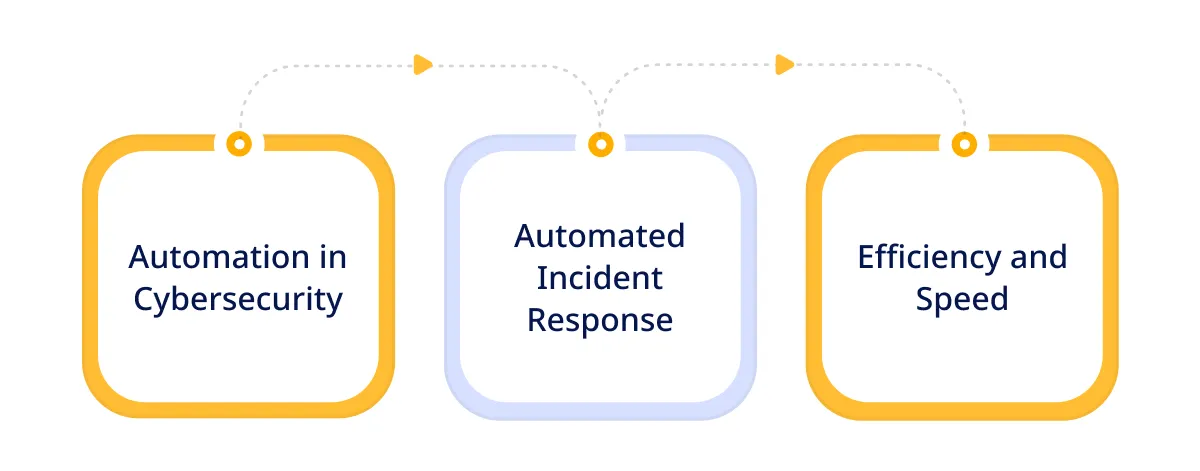
- Automation in Cybersecurity: It uses advanced algorithms and machine learning to detect & respond to threats in real-time, significantly reducing the time between detection and action.
- Automated Incident Response: Automated systems can take predefined actions to mitigate threats without requiring human intervention.
- Efficiency and Speed: The primary advantages of automation in cybersecurity are efficiency and speed. Automated threat mitigation systems operate 24/7, ensuring constant vigilance and rapid response to incidents.
Adaptability to Emerging Threats
The world of cyber threats is continually changing, with new vulnerabilities and attack vectors.This dynamic environment requires the top software security tips that can adapt quickly to stay ahead of potential attacks.
However, there are some static security solutions available in the marklet, but they can quickly become obsolete with time and leave organizations vulnerable to new types of attacks.
That’s why advanced threat detection systems utilize adaptive learning technologies viz. machine learning and AI solutions for IT, to continuously learn & adapt to new threats.
- These systems analyze large amounts of data, identify patterns, and update their detection algorithms in real-time.
- They recognize and respond to novel threats that traditional security measures might miss.
- They provide robust protection against the latest threats in modern businesses.
Moreover, Adaptive learning ensures that the security infrastructure remains effective against both known and unknown threats, thus, providing a proactive defense mechanism that evolves alongside the threat landscape.
Use advanced technology to safeguard your data.
Case Studies of Successful Implementations
By adopting cutting-edge technologies and proactive security measures, organizations can effectively protect their digital assets, ensure business continuity, and build trust with their stakeholders.
Here are a few examples showing the effectiveness of advanced threat detection in strengthening cybersecurity:
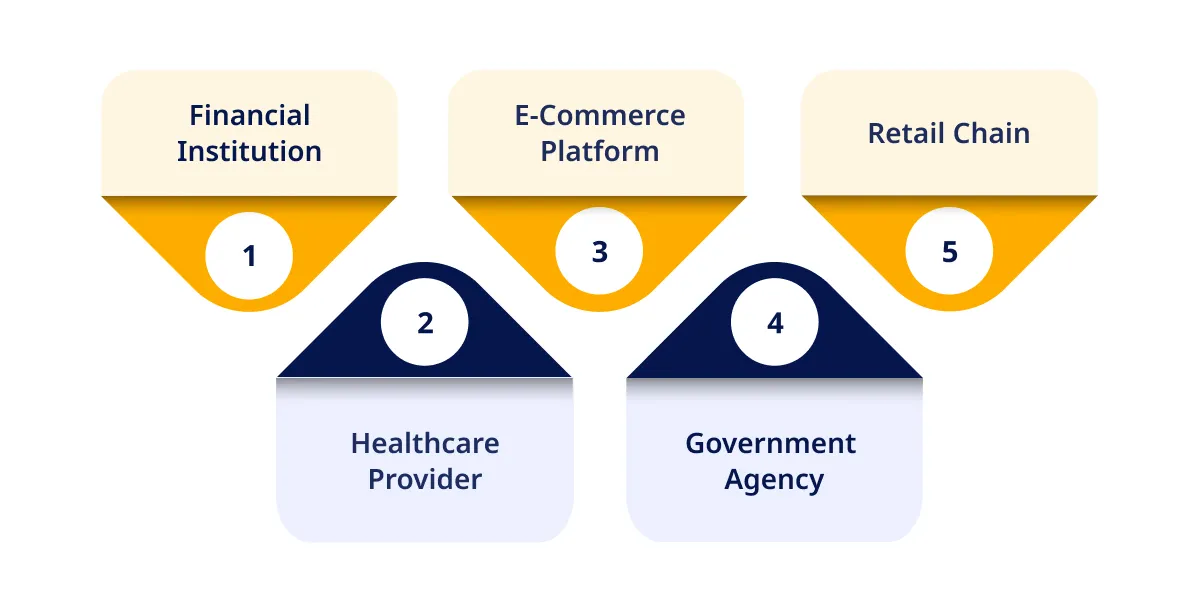
1. Financial Institution for Proactive Fraud Prevention
A leading financial institution faced continuous threats from cybercriminals attempting to breach its systems & defraud customers.
By implementing an advanced threat detection system that utilized machine learning & behavioral analysis, the institution was able to monitor transactions in real-time & identify suspicious activities.
Also read: Top Data Engineering Companies to Watch in 2025
2. Healthcare Provider for Ransomware Defense
A large healthcare provider was targeted by a sophisticated ransomware attack that threatened to encrypt patient data and disrupt operations.
The organization had recently deployed an advanced threat detection solution with real-time monitoring and automated response capabilities. The system detected unusual file encryption activities and immediately isolated the affected systems.
3. E-Commerce Platform for Enhanced Customer Protection
An e-commerce platform handling vast amounts of customer data needed a robust solution to defend against evolving cyber threats.
By integrating dark web monitoring and OSINT into their advanced threat detection framework, the platform could identify and address threats before they materialized into full-blown attacks.
4. Government Agency for Comprehensive Network Security
A government agency tasked with protecting sensitive national data faced the challenge of safeguarding against a wide array of cyber threats.
Implementing an advanced threat detection system with comprehensive threat intelligence capabilities allowed the agency to monitor its network continuously and respond to threats in real-time.
5. Retail Chain for Securing Point-of-Sale Systems
A large retail chain experienced repeated attempts to compromise its point-of-sale (POS) systems, putting customer payment information at risk.
The retailer deployed an advanced threat detection solution that utilized sandboxing and behavioral analysis to monitor POS activities. The system quickly identified and isolated malware trying to infiltrate the network.
Implement advanced threat detection for comprehensive protection.
Final Words
As cyber threats grow in complexity & frequency, the need for advanced threat detection has never been more critical. By integrating innovative technologies & proactive strategies, organizations can safeguard their digital assets & maintain customer trust.
From real-time monitoring to predictive analytics, the advancements in threat detection are reshaping the cybersecurity landscape, making it possible to detect & neutralize threats before they cause harm.
Let’s connect with our experts at ValueCoders (a leading application testing services company in India) as they use these cutting-edge solutions to fortify defenses and ensure a resilient and secure future in an increasingly digital world.