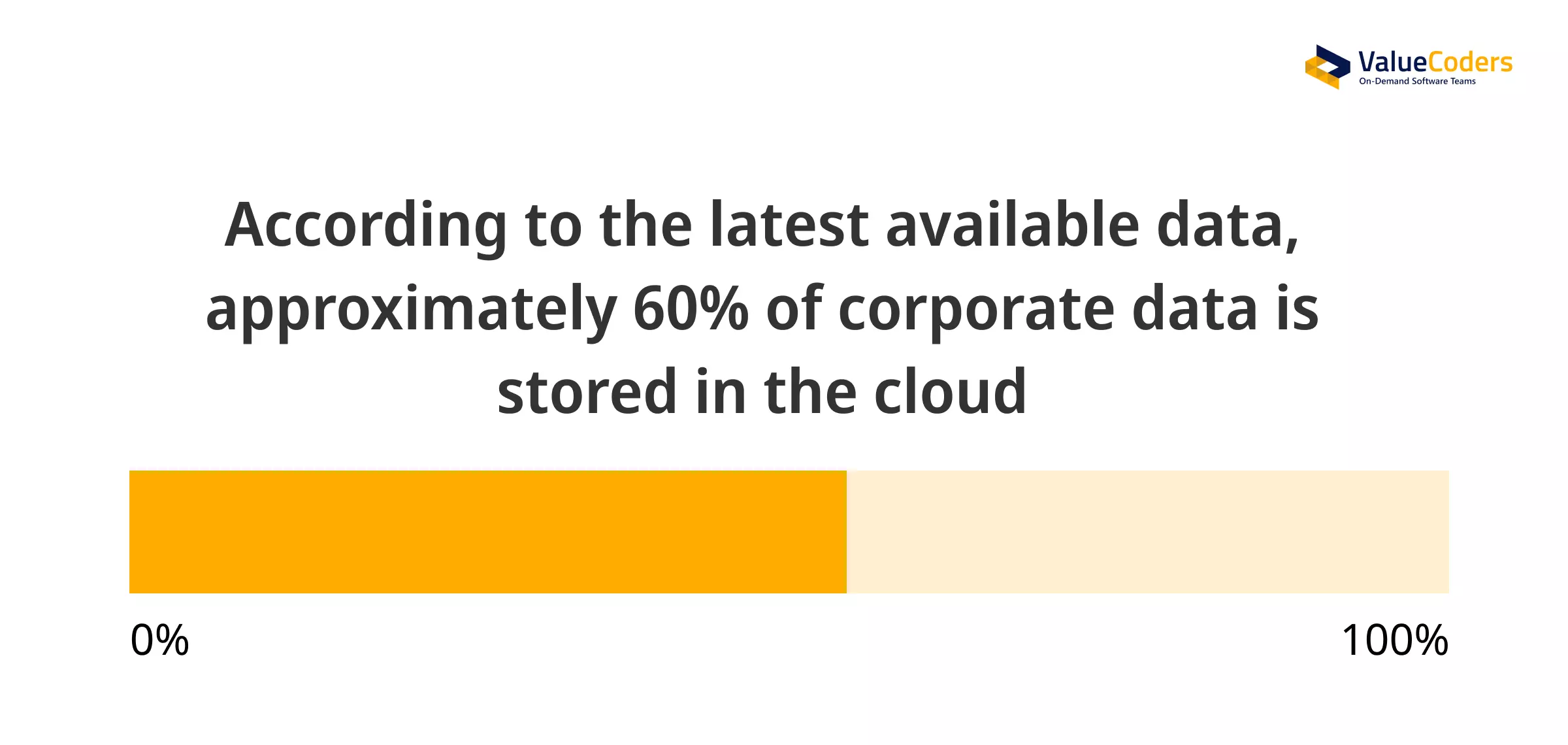
As per Statista, enterprises store 60% of the data on the cloud, whereas the average employee uses 36 cloud-based services daily. This heavy reliance on cloud services makes security not just important for software companies—but essential.
This growing need for stronger cloud security is an alarm to enterprises to act fast and integrate cloud solutions.
Their security concern must be embedded into SaaS development from the start. A proactive approach—integrating DevSecOps, encryption, and automated security testing—helps create robust software as a service without slowing down innovation.
Understanding SaaS App Security
SaaS platforms hold vast amounts of private and confidential information, financial records, business strategies, and whatnot. Any threat or compromise in security can lead to big issues or even a complete company shutdown.
When we talk about cloud software security, we’re focusing on three core principles:
- Protecting Applications from Cyberattacks
- Safeguarding Sensitive Information
- Maintaining Regulatory Compliance
The Role of DevOps in Security
DevOps has long bridged the gap between development and operations, with security as a key focus. By working together, teams ensure software runs smoothly and remains secure.
The rise of DevSecOps further integrated security into every phase of development. Automated security testing now detects vulnerabilities early, enhancing protection.
However, evolving cyber threats demand even more advanced DevOps practices. Traditional DevSecOps alone may not suffice. Continuous monitoring, automated compliance checks, DAST, zero-trust architecture, and policy as code (PaC) are now essential for robust security.
Partnering with the top DevOps engineers in India can help businesses implement seamless security automation and achieve operational efficiency.
We enhance real-time monitoring and incident response to prevent costly security breaches.
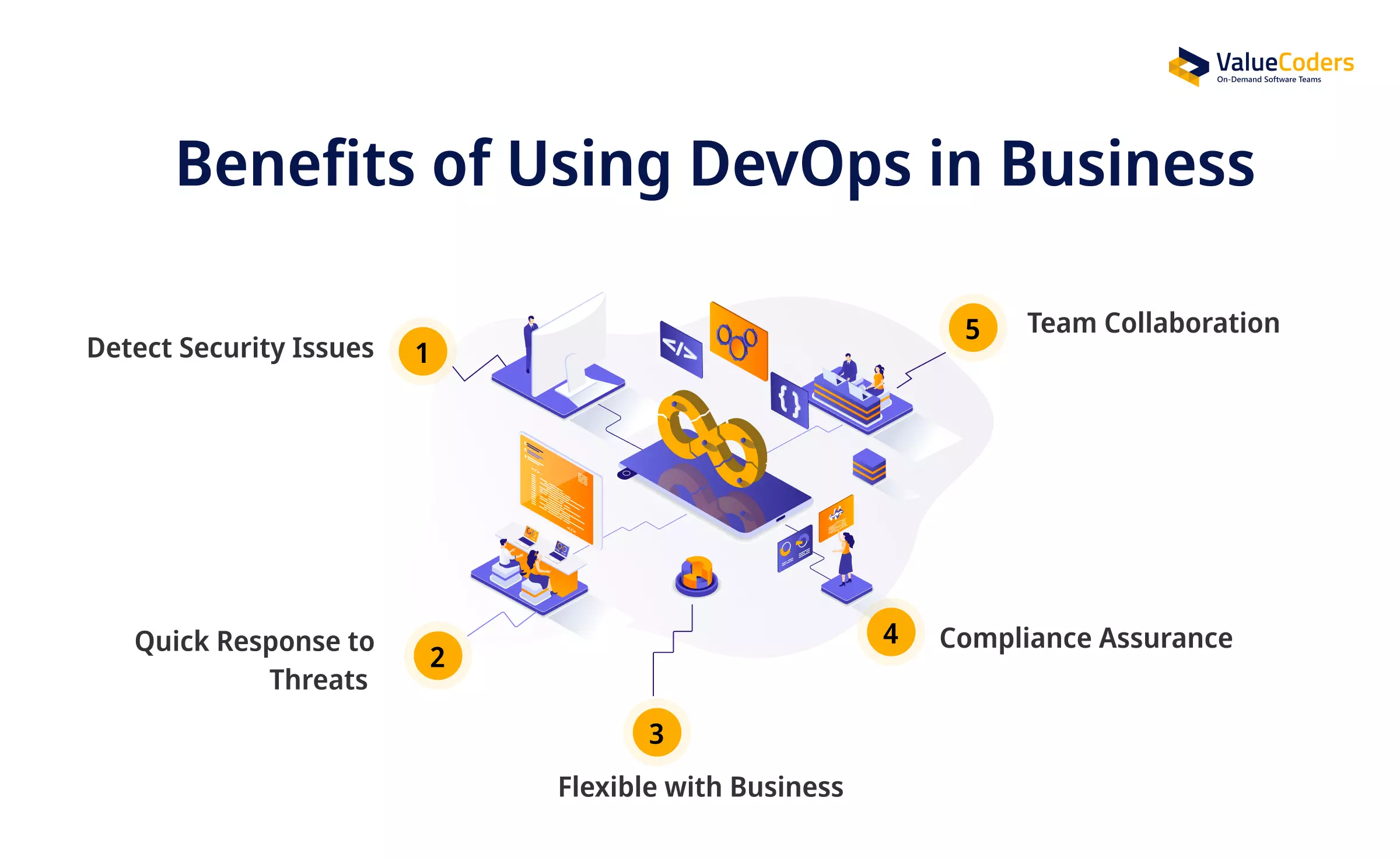
Key Benefits of Integrating Security in DevOps
Protecting phishing and data attacks is a big concern of SaaS app security. Integrating DevOps security automation and other best practices provides a safe infrastructure for businesses.
Here’s why security in DevOps is a smart choice:
1. Detect Security Issues Early
Automatic testing in the development process helps find security problems before they become serious.
- Stops hackers from stealing data or causing harm.
- Keeps systems running safely without sudden security failures.
2. Quick Response to Threats
- Monitors systems all the time and sends alerts when something goes wrong.
- Helps teams fix security issues quickly to reduce damage.
- Protects customer accounts and prevents financial losses.
3. Flexible with Business
- Security tools adjust as your business grows without slowing down new updates.
- Uses cloud security tools to protect data in online storage.
- Keeps security strong without affecting performance.
4. Compliance Assurance
- Checks security automatically to follow rules like GDPR, HIPAA, and SOC 2.
- Prevents costly fines for breaking security laws.
- Ensures that security is built into the software from the start.
5. Team Collaboration
- Encourages teamwork between developers, operations, and security teams.
- Everyone works together to make safe and reliable software.
- Speeds up the process of fixing security problems.
Also read: SaaS Development Secrets For Modern Business Products
Steps to Ensure SaaS App Security with DevOps
DevOps prioritizes safety from the start so you can catch vulnerabilities before they become a problem. This way, you can keep your customers’ trust and protect your business from harm. Therefore, SaaS security is not an afterthought.
Steps for SaaS security best practices with DevOps:
1. Security-First Mindset
Security is a big concern for everyone. Creating a culture where security is everyone’s responsibility forms the foundation of a robust security strategy.
Key Actions:
- Educate teams about the importance of security and its role in development
- Foster collaboration between developers, operations, and security experts
- Incorporate security objectives into performance evaluations and KPIs
- Host regular security awareness training sessions
- Create clear security incident response procedures
- Encourage reporting of potential security concerns
- Establish security champions within development teams
2. Secure Code Development
The foundation of any secure SaaS application lies in its code. By implementing secure coding practices from the start, you can prevent many common vulnerabilities before they become issues.
Key Actions:
- Use secure coding practices to minimize vulnerabilities
- Implement code review processes to ensure adherence to security standards
- Leverage static application security testing (SAST) tools for real-time vulnerability detection
- Follow secure coding guidelines like OWASP Top 10
- Document security requirements in code repositories
- Implement version control with security checks
- Conduct regular code audits
3. Automated Security Testing
Automation is key to maintaining security at DevOps speed. A security testing service implements best practices to catch vulnerabilities early and ensures consistent security checks throughout the development pipeline.
Key Actions:
- Integrate automated tools for dynamic application security testing (DAST)
- Use dependency scanning tools to identify vulnerabilities in third-party libraries
- Conduct regular penetration testing to simulate real-world attacks
- Implement automated security gates in CI/CD pipelines
- Schedule regular automated security scans
- Set up automated vulnerability reporting
- Create automated remediation workflows
Our security-first DevOps approach keeps your platform safe from cyber threats and compliance risks.
4. Continuous Monitoring
Real-time visibility into your application’s security status is crucial. Continuous monitoring helps detect and respond to security threats before they can cause significant damage.
Key Actions:
- Deploy real-time monitoring systems for anomalous activities
- Use log management solutions to track and analyze application behavior
- Implement a centralized dashboard for unified security oversight
- Set up automated alerts for security incidents
- Monitor user behavior analytics
- Track system performance metrics
- Implement automated incident response
5. Access Control and Authentication
Controlling who has access to what within your SaaS application is fundamental to security. Strong authentication and access controls help prevent unauthorized access and potential data breaches.
Key Actions:
- Enforce multi-factor authentication (MFA) for user accounts
- Use role-based access control (RBAC) to limit permissions
- Regularly review access logs to detect unauthorized attempts
- Implement session management controls
- Set up IP-based access restrictions
- Create strong password policies
- Maintain detailed access to audit trails
6. Data Encryption and Protection
Protecting sensitive data through encryption is non-negotiable in today’s security landscape. Proper encryption practices help ensure data security both in transit and at rest.
Key Actions:
- Encrypt sensitive data both in transit (SSL/TLS) and at rest (AES-256)
- Use tokenization to protect data identifiers
- Employ secure key management systems for encryption keys
- Implement data masking for sensitive information
- Set up secure backup encryption
- Create data classification policies
- Establish data retention guidelines
7. Maintain Regular Updates and Patching
Keeping your systems updated is crucial for maintaining security. Regular updates and patches help protect against known vulnerabilities and security threats.
Organizations can invest in SSL certification to secure data transmission and improve overall security.
Key Actions:
- Schedule routine updates to address software vulnerabilities
- Use automated patch management tools to ensure timely fixes
- Test patches in a staging environment before deployment
- Maintain a patch management policy
- Document update procedures
- Create rollback plans
- Monitor patch effectiveness
Secure SaaS applications with a balanced approach that combines automation, continuous monitoring, and a robust work culture. SaaS development services ensure all elements are followed to build a secure application.
Protect your SaaS from cyberattacks and downtime with our robust DevSecOps strategies.
Real-World Applications and Case Studies
Case Study 1: Netflix
Netflix’s DevSecOps approach includes automated security checks during CI/CD pipelines, ensuring rapid deployment without compromising security.
Case Study 2: Shopify
Shopify implements robust encryption and automated monitoring tools to protect customer data and comply with industry standards.
Also read: What Is SaaS? Here’s The List Of Top 8 Benefits And More
Common SaaS Development Challenges and Solutions
The journey of building a successful Software as a Service (SaaS) application is paved with opportunity and its associated challenges. While developing the product the challenges are always there. However, SaaS consulting services will help you overcome those problems, providing a smooth development of the application.
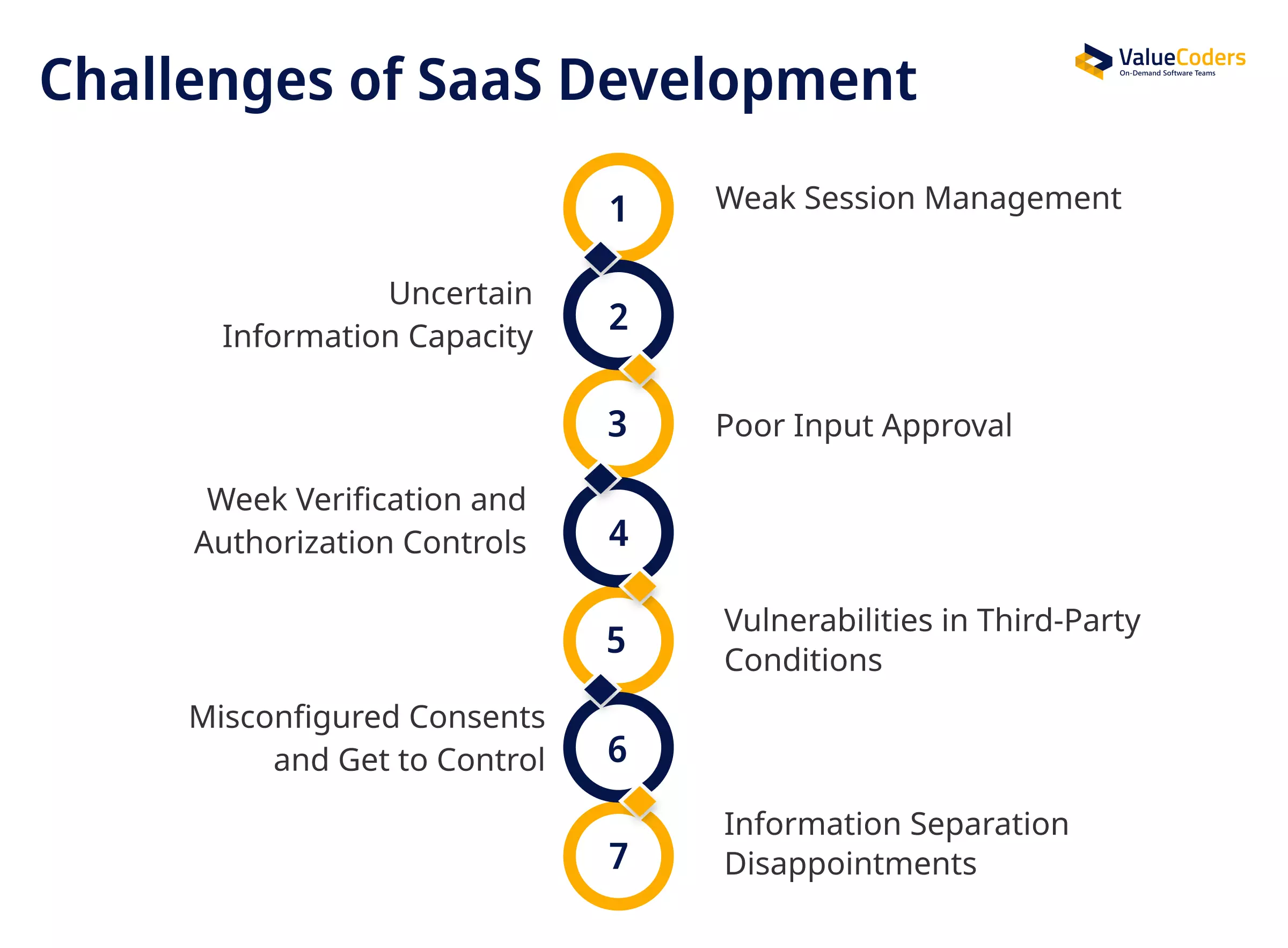
Let’s delve into some of the common SaaS application development challenges and explore practical solutions to overcome them:
1. Weak Session Management
Challenge: Imagine a scenario where a malicious actor gains control of a user’s active session. This “session hijacking” could expose sensitive user data, leading to severe security breaches and reputational damage.
Solution: A robust approach to session management is crucial. Implementing session timeout policies automatically terminates inactive sessions, reducing the window of opportunity for hijacking. Using secure cookies, marked with the “HttpOnly” and “Secure” flags, helps prevent unauthorized access through client-side scripts.
2. Uncertain Information Capacity
Challenge: Poorly managed data storage can create vulnerabilities. If not handled carefully, sensitive customer data might be unintentionally exposed, risking privacy violations and severe legal consequences.
Solution: Embrace secure cloud storage solutions designed with security in mind. Employ encryption both in transit (while data is being transferred) and at rest (when data is stored). This ensures that even if a breach occurs, the data is indecipherable to unauthorized parties.
3. Poor Input Approval
Challenge: User inputs are like open doors – they can be exploited by attackers. Malicious code injected via these inputs (such as SQL injection) can corrupt databases, disrupt services, or compromise user information.
Solution: Treat all user inputs as potentially harmful. Employ input validation using techniques like whitelisting (allowing only known, safe characters and patterns) and regular expressions (defining specific rules for data format) to meticulously filter out any malicious content.
4. Week Verification and Authorization Controls
Challenge: Relying on outdated or basic authentication methods opens the door to unauthorized access. Weak passwords and easily guessed credentials make your SaaS application an easy target.
Solution: Enhance security with Multi-Factor Authentication (MFA), which requires multiple verification steps before granting access. Implement Role-Based Access Control (RBAC), which assigns permissions based on user roles, ensuring that users only have access to what they absolutely need.
5. Vulnerabilities in Third-Party Conditions
Challenge: SaaS applications often rely on external libraries, APIs, and other third-party components. These dependencies, if not carefully managed, can introduce security vulnerabilities and hidden bugs into your system.
Solution: Make a habit of regularly updating third-party libraries to the latest stable versions. Also, implement regular audits to ensure that these components don’t have known security flaws that attackers can exploit.
6. Misconfigured Consents and Get to Control
Challenge: Giving too much access to users or administrators creates serious risks. Accounts with overly broad permissions are the prime targets for malicious activity.
Solution: Conduct routine access control reviews. Implement the principle of least privilege, ensuring that users and administrators have only the minimum permissions necessary for their tasks. Use an automated process to enforce user access policies effectively.
7. Information Separation Disappointments (Multi-Tenancy Dangers)
Challenge: SaaS applications often operate on a multi-tenant architecture. This can cause data leakage – one customer’s data being accessed by another, which is a critical security and compliance breach.
Solution: DevOps carefully manages the business infrastructure, avoiding data vulnerability. Enforce sticky data policies and follow security measures for each tenant using multi-tenant architecture.
Speed up your response time with DevOps-driven automation and real-time security insights.
Conclusion
DevOps keeps SaaS businesses secure by performing thorough security testing.
By adopting SaaS security best practices and collaborating with a premier DevOps consulting firm like ValueCoders, businesses can effectively develop secure, reliable, and regulation-compliant applications that meet the demands.
If you are ready to use secure DevOps solutions tailored for SaaS applications. Our expert team handles businesses to implement:
- Automate security testing to detect vulnerabilities early.
- Continuous monitoring for real-time threat detection.
- Robust Access Control & Encryption o safeguard sensitive data.
- Compliance Assurance for GDPR, HIPAA, SOC 2, and more
Contact us to build a secure, reliable, and scalable SaaS product together.