Safeguarding Intellectual property is a growing security concern among modern businesses.
An ABI Research report claims the cost of intellectual property theft falls between $180 billion and $540 billion annually in the United States alone. The thefts have also impacted more than 45 million jobs in the country.
Are you also afraid of loosing your company’s confidential information, and want to secure your Intellectual Property while software outsourcing?
Let’s explore the top outsourcing IP protection strategies and best practices to safeguard your Intellectual Property.
Understanding Intellectual Property (IP)
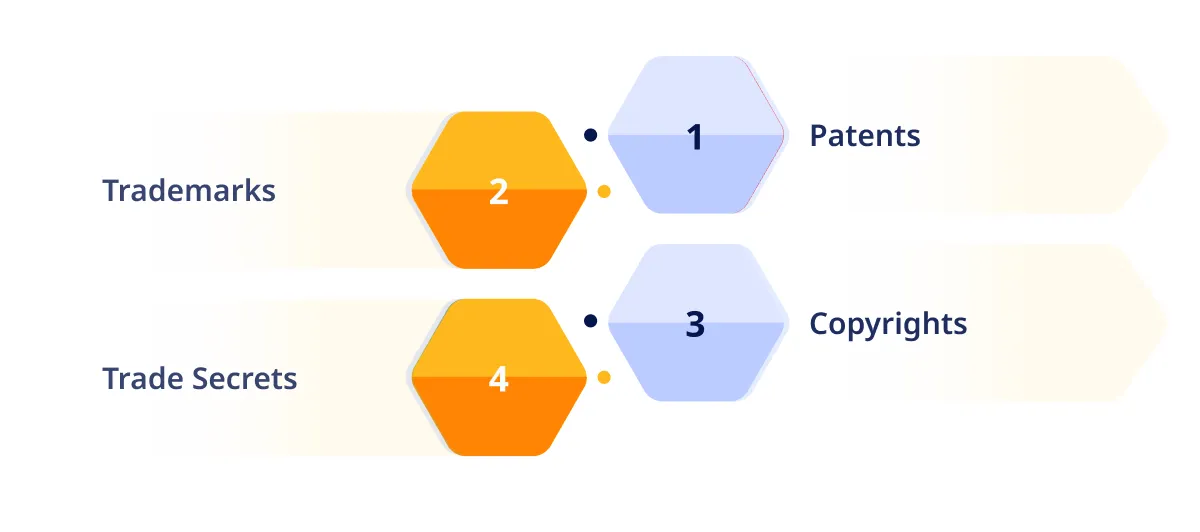
Intellectual Property is termed as the creations of the mind that are legally protected from unauthorized use by others. These creations can be inventions, literary, artistic works, and designs. The various types of IP are given below:
- Patents: They protect new inventions/discoveries, granting the patent holder pure rights to sell, use, and manufacture the invention for a specific period, usually 20 years from the filing date.
- Trademarks: These are symbols, names, phrases, logos and designs. They differentiate the goods and services of one entity from those of others.
- Copyrights: They protect original creation of authorship, such as music, books, films, software etc. This gives the owner/creator complete rights to use and share the work for a specified period, typically the life of the author plus 70 years.
- Trade Secrets: Trade secrets encompass confidential information of businesses that provides them a competitive edge, such as processes, formulas, practices, designs, or a compilation of information.
We've helped countless businesses protect their IP. Let our experts guide you to peace of mind.
Importance of IP for Maintaining Competitive Advantage
Intellectual Property provides several key advantages for businesses, as discussed below:
1. Exclusivity: IP protection grants exclusive rights to use and exploit creations, preventing competitors from copying or using them without permission.
2. Brand Value: Trademarks and copyrights build brand recognition and loyalty, distinguishing products and services in the market.
3. Revenue Generation: Patents and copyrights can be licensed or sold, generating significant revenue streams.
4. Market Position: IP helps maintain a competitive edge by safeguarding innovations and unique aspects of a business, preventing competitors from easily replicating them.
5. Investment Attraction: Strong IP portfolios can attract investors and partners, demonstrating a company’s innovation and potential for growth
Examples of IP in Various Industries
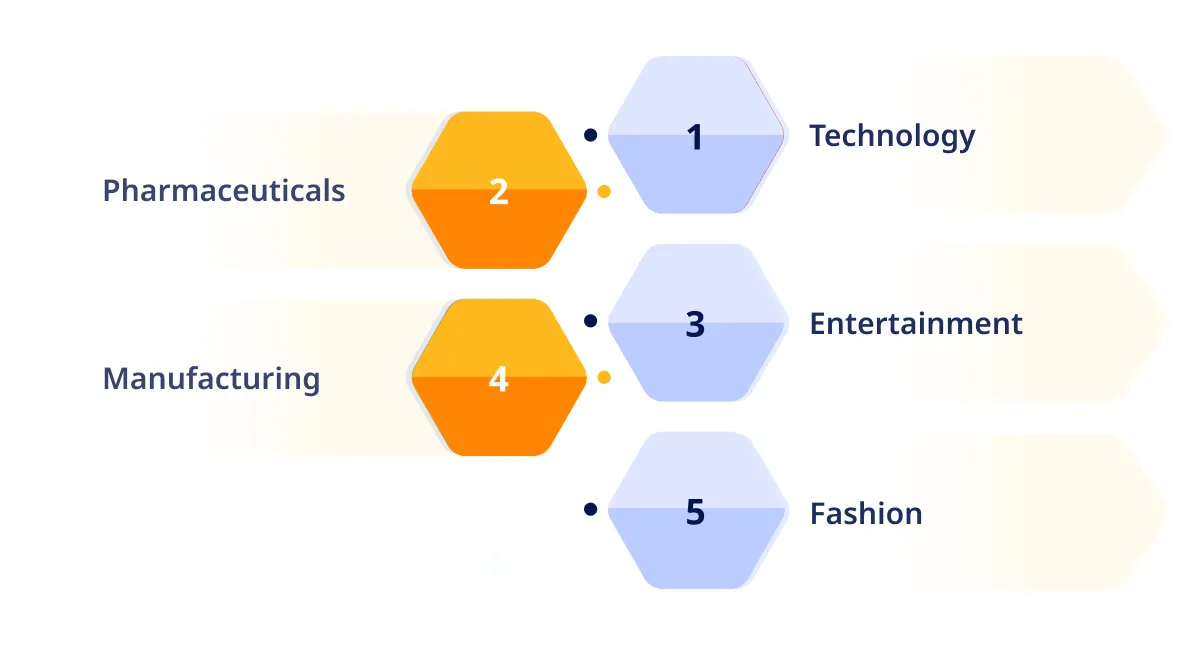
Understanding and effectively managing your Intellectual Property is crucial, especially when outsourcing IP protection. Have a look at the key use cases of IP in different industries:
1. Technology: Patents for innovative hardware designs, software algorithms, and trademarks for brand names like Apple and Google.
2. Pharmaceuticals: Patents for new drugs and treatments, along with trade secrets related to the drug formulation process.
3. Entertainment: Copyrights for movies, music, books, and video games.
4. Manufacturing: Trade secrets for proprietary manufacturing processes and designs, trademarks for product names and logos.
5. Fashion: Trademarks for brand names and logos, copyrights for unique designs.
Also Read: Top 15 IT Staff Augmentation Service Companies
Assessing the Risks of Outsourcing
Have a look at the real and tangible risks associated with outsourcing IP protection as discussed below:
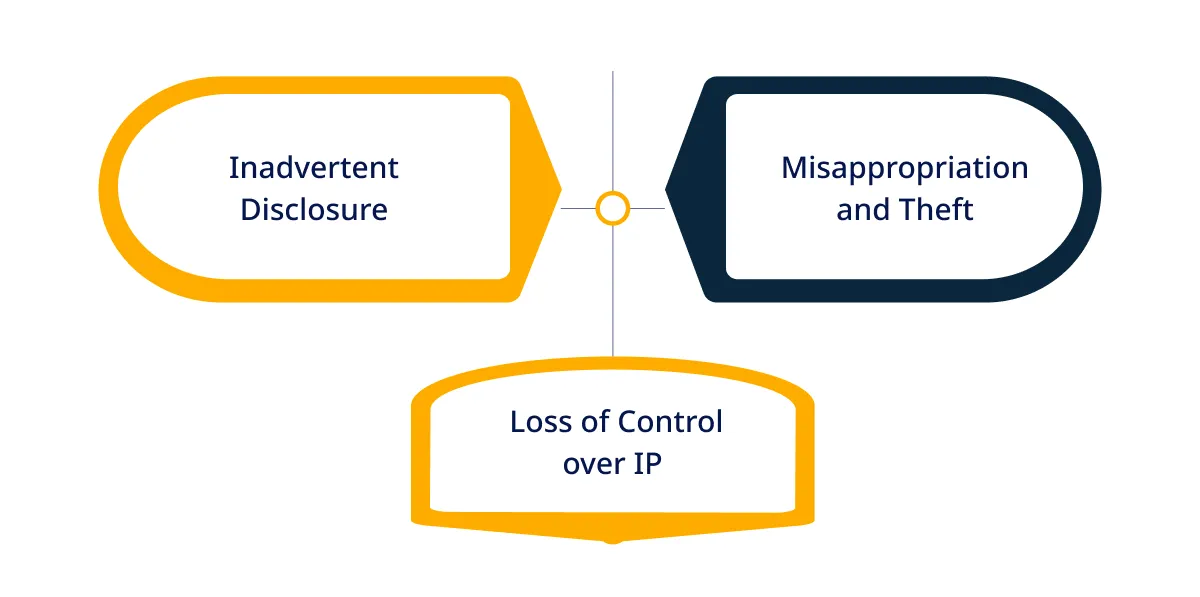
Common IP Risks Associated with Outsourcing
You may encounter the following IP risks while outsourcing your business needs:
1. Misappropriation and Theft
When you share your Intellectual Property with an external partner, there is always a risk of it being stolen or misused. This could involve a partner using your proprietary information to develop competing products or staff augmentation services or selling it to your competitors.
2. Inadvertent Disclosure
Even with the best intentions, outsourced partners can accidentally disclose your confidential information. This might happen through insecure communication channels, inadequate data protection measures, or a lack of awareness about the sensitivity of the information.
3. Loss of Control over IP
IT Outsourcing services may lead to a loss of control over how your IP is used and protected. Without direct oversight, you might not be able to enforce your IP policies effectively, leading to potential breaches and misuse.
Real-World Examples of IP Issues in Outsourcing
The following examples show the risks associated with outsourcing IP protection and underscore the need for robust IP protection strategies.
Example 1: Tech Industry Breach
A well-known technology company outsourced part of its software development to a third-party vendor. Hiring remote developers helped them a lot to achieve their goals.
Despite non-disclosure agreements, the vendor’s lax security practices led to the inadvertent leak of source code, which competitors subsequently used to create a similar product.
Example 2: Pharmaceutical Theft
A pharmaceutical firm faced a significant setback when a foreign manufacturing partner was found to be reverse-engineering their proprietary drug formulation.
The partner then launched a generic drug version, significantly impacting the firm’s market share and revenue.
Example 3: Manufacturing Leak
A major electronics manufacturer outsources production to a factory overseas. They hire Indian developers to get their tasks done.
However, due to insufficient oversight, detailed schematics of their new product were leaked, leading to counterfeit versions flooding the market before the official launch.
Partner with us for IP-safe outsourcing practices that minimize risk and unlock growth potential.
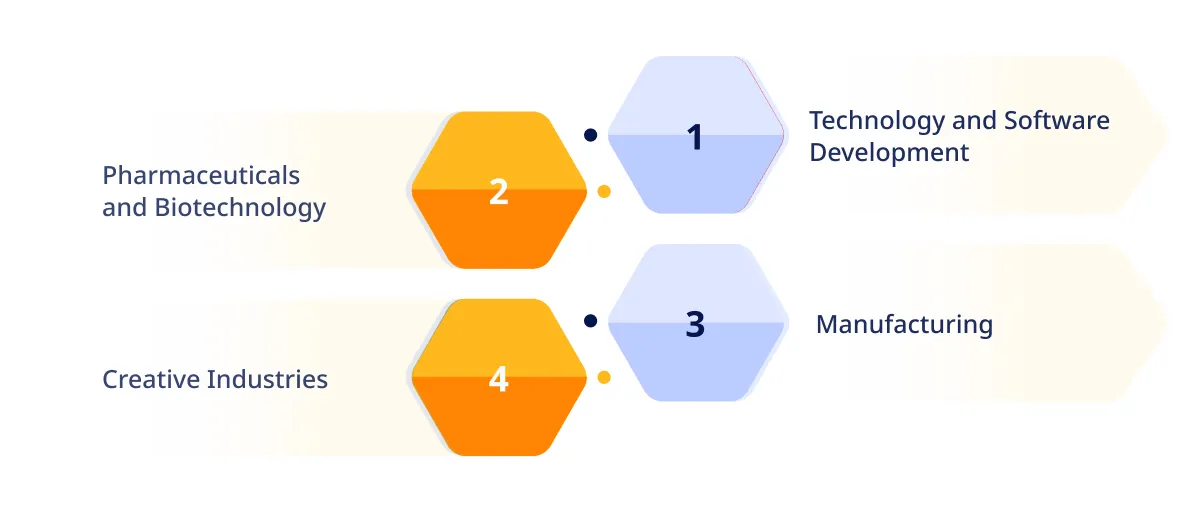
Industries Most at Risk
Certain industries are particularly vulnerable to IP risks due to the nature of their work and the value of their intellectual assets:
1. Technology and Software Development
With rapid innovation and high-value proprietary algorithms, the tech industry is a prime target for IP theft.
2. Pharmaceuticals and Biotechnology
The extensive research and development in these sectors make them susceptible to misappropriating trade secrets and patents.
3. Manufacturing
Industries reliant on unique processes or proprietary designs face significant risks when outsourcing production to third parties.
4. Creative Industries
Media, entertainment, and fashion sectors are vulnerable due to the high value of their creative content and designs.
Questions to Ask Your Development Partner to Protect IP Outsourcing
There are some common questions you must ask your offshore software development partner while outsourcing IP protection:
1. How will you protect my company’s data and information?
2. What security measures will you take to ensure the confidentiality of my business information?
3. Will my company keep 100% of the rights to the software developed?
4. Have you ever had any prior data breaches or IP rights outsourcing conflicts?
5. Can you provide your internal IP safety protocols?
6. What do you do to safeguard your and our Intellectual Property?
7. What about the safety protocols when exchanging documents and sensitive information?
Also Read: Cracking the Code: Overcoming Challenges in Outsourcing to India
6 Top Ways for Safeguarding IP When Outsourcing
Have a look at the key six strategies to safeguard outsourcing IP protection for your business success:
1. Selecting the Right Outsourcing Partner
Approaching the right software outsourcing partner is the first most essential key to safeguard intellectual property.
Criteria for Choosing The Right Partner
Here are some essential criteria and due diligence steps to ensure you choose a reliable partner:
1. Reputation and Track Record
- Go for a company with a proven track record in your industry or technology area. Longevity and success in the field often indicate reliability.
- Seek testimonials and reviews from past clients to gauge their satisfaction and trust in the partner.
- Review case studies or portfolios that showcase the partner’s previous work and IP management practices.
2. Security Measures and Certifications
- Ensure the partner has robust data security measures, including encryption, secure servers, and access controls.
- Look for relevant industry certifications that promise a commitment to data security.
- Verify that the partner complies with international data protection regulations, such as GDPR or CCPA.
3. IP Policies and Practices
- Evaluate the partner’s policies for handling and protecting IP. This includes how they manage sensitive information and their procedures for preventing IP theft.
- Ensure the partner’s employees have signed agreements including confidentiality and IP assignment clauses.
- Check if the partner regularly trains their staff on IP protection and security protocols.
Due Diligence Process
Have a look at the due diligence process in order to choose the reliable partner:
1. Conducting Background Checks
- Research the company’s history, including any legal issues or past IP disputes.
- Verify the backgrounds of the company’s founders and leadership team to ensure they have a solid reputation.
- Use professional networks and industry associations to gather insights into the partner’s reputation.
2. Evaluating References and Past Projects
- Ask for references from potential clients to understand their experiences with the partner.
- Request samples of past projects to assess the quality of their work and their adherence to IP protection practices.
- Look for documented success stories where the partner has effectively managed and protected IP for other clients.
3. Assessing Financial Stability
- Review financial statements or reports to ensure the partner is financially stable and capable of fulfilling long-term commitments.
- Evaluate whether the partner invests adequately in security infrastructure and employee training.
- Check if the partner has business continuity, and disaster recovery plans that ensure your IP remains secure even in adverse situations.
2. Crafting a Strong Contract
By crafting a strong contract with clear software outsourcing clauses, you can significantly mitigate the risks associated with outsourcing IP protection.
Key Elements of IP Protection in Contracts
Have a look at the key elements involved in IP protection in contracts.
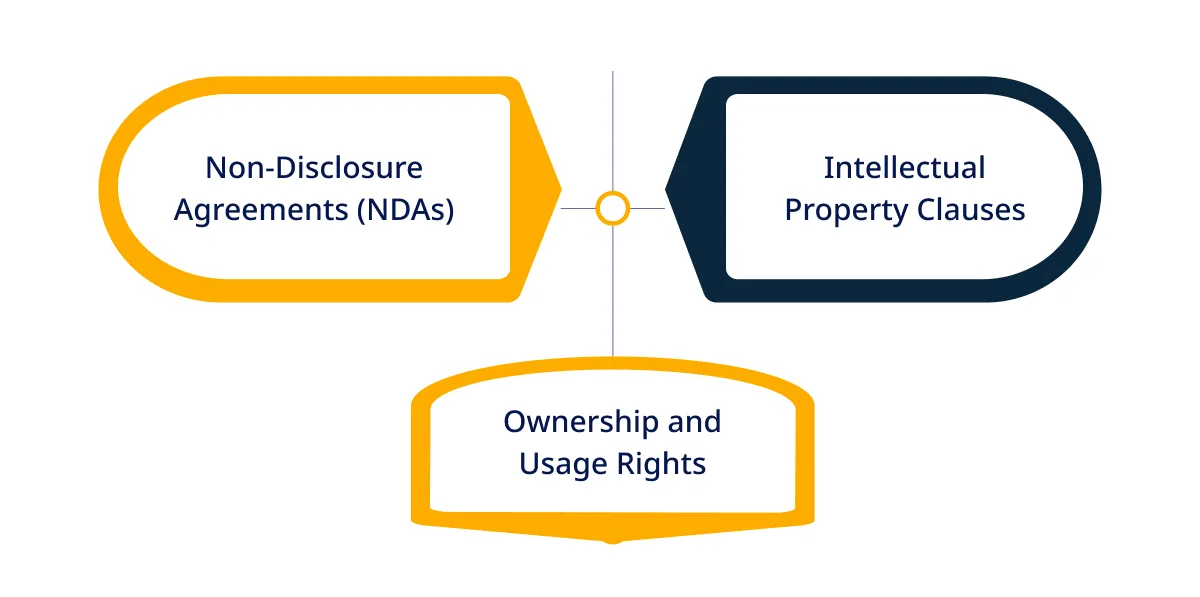
1. Non-Disclosure Agreements (NDAs)
NDAs are essential for protecting your Intellectual Property. They legally bind the outsourcing partner to confidentiality, ensuring they cannot disclose or misuse your proprietary information.
2. Intellectual Property Clauses
Need to clearly define usage and ownership rights of the IP created during the project. Specify that all IP developed during the collaboration remains your exclusive property.
3. Ownership and Usage Rights
Establish who will own the IP and how it can be used. Ensure that the contract stipulates that you retain full ownership and the rights to use, modify, and distribute the developed software.
Specific Provisions to Include
Have a look at the other specific provisions to include in safeguarding IP.
1. Confidentiality Obligations
Detail the responsibilities of the outsourcing partner in maintaining the confidentiality of your IP. This should include measures for protecting sensitive information and consequences for failing to do so.
2. IP Ownership and Transfer
Include clauses that specify the transfer of IP ownership to you upon completion of the project. Ensure there are no ambiguities about who owns the IP and that all rights are transferred to you.
3. Consequences of Breach
Clearly outline the consequences if the outsourced software product development company breaches the contract. This can include financial penalties, legal actions, and termination of the agreement.
Tips for Negotiating Favorable Terms
Have a look at the following tips for negotiating favourable terms:
1. Be Clear and Specific
Ensure that all terms related to IP protection are clearly defined and specific. Avoid any fuzzy language that could lead to misunderstandings/disputes.
2. Consult Legal Experts
Work with legal professionals who are experts in IP and outsourcing contracts. They can help you draft robust agreements that protect your interests.
3. Negotiate Early
Discuss IP protection terms early in the negotiation process. This will set the tone for the collaboration and ensure that both parties understand the importance of safeguarding IP.
4. Leverage Your Position
Use your position as the client to negotiate favorable terms. Make it clear that protecting your IP is a non-negotiable aspect of the partnership.
Our contracts ensure that your sensitive information remains confidential and secure.
3. Implementing Security Measures
By implementing robust security measures, you can significantly reduce the risks associated with outsourcing IP protection and ensure that your Intellectual Property remains protected.
Physical and Digital Security Practices
Let’s know about the physical and digital security practices for safeguarding IP:
1. Data Encryption and Secure Communication Channels
Encrypt all sensitive information to protect it from unauthorized access. Use secure communication channels like VPNs and SSL/TLS protocols to ensure data integrity and confidentiality.
2. Access Controls and Monitoring
Deploy strict access control measures to limit access to your Intellectual Property. Role-based access controls ensure that only authorized users have access to sensitive data.
3. Regular Security Audits
Conduct regular security audits to check and address potential issues in your systems. These audits should cover both physical as well as digital security practices to ensure comprehensive protection of your Intellectual Property.
Best Practices for Handling Sensitive Information
Have a look at the key practices for handling sensitive information:
1. Minimizing Data Sharing
Limit the sharing of sensitive information to only what is necessary for the completion of the project. The less data is shared, the lower the risk of unauthorized access or misuse.
2. Segregation of Duties
Implement segregation of duties (SoD) to reduce the risk of fraud and errors. Ensure that critical tasks and responsibilities are divided among different individuals or teams to prevent any single person from having too much control over sensitive information.
3. Secure Storage and Disposal
Store sensitive data securely using encryption and secure storage solutions. When data is no longer needed, ensure it is disposed of securely using methods such as physical destruction of storage media or data wiping.
4. Educating and Training Your Team
Internal awareness and training safeguard your Intellectual Property when using software outsourcing services. You must ensure that dedicated development teams understand IP protection clauses and is well-equipped to handle potential risks can significantly reduce vulnerabilities.
There are fewer chances that educated employees make mistakes that could further lead to IP breaches. The proper training ensures that all team members follow the same protocols, creating a unified approach to IP protection.
- Teach employees how to recognize potential IP risks, such as phishing attempts, insecure data transfer methods, and unauthorized access.
- Train employees on the importance of encrypting sensitive information during storage and transmission.
- Promote the maximum usage of secure communication channels, such as encrypted emails and secure file-sharing platforms.
- Emphasize the importance of following company security policies and procedures to protect IP outsourcing.
- Encourage employees to stay informed about the latest security protocols and updates.
- Conduct regular training sessions to make employees aware of the latest outsourcing IP safety tips.
- Organize workshops as well as seminars led by industry experts to provide deeper insights into IP protection.
- Share updates on new best practices and technological advancements that can enhance IP security.
- Implement a feedback process to collect insights from employees on the effectiveness of training programs and areas for improvement.
5. Ongoing IP Management and Monitoring
Continuous IP management and monitoring are essential for outsourcing IP protection. By establishing regular monitoring processes and utilizing appropriate tools, you can detect and address potential IP breaches promptly.
Setting Up Regular Monitoring and Auditing Processes
Here are the practices you must follow for regular monitoring:
1. Scheduled Audits: Conduct regular audits of your outsourcing partner’s processes and systems to ensure compliance with IP protection protocols. Audits should cover data access logs, employee activities, and adherence to security measures.
2. Performance Reviews: Implement periodic reviews to assess the effectiveness of IP protection strategies and make necessary adjustments.
3. Compliance Checks: Regularly check for compliance with contractual obligations related to IP protection. Ensure that the outsourcing partner follows agreed-upon procedures and standards.
Tools and Technologies for Tracking IP Usage and Compliance
Have a look at the following tools/technologies for safeguarding IP:
- IP Management Software: Utilize specialized software to manage and track IP assets. These tools can help monitor usage, detect unauthorized access, and ensure compliance with IP policies.
- Data Analytics: Leverage data analytics to identify unusual patterns or activities that might indicate IP misuse or breaches. Analytics tools can provide insights into how IP is being used and accessed.
- Automated Alerts: Set up automated alerts to notify you of any suspicious activities or potential breaches. These alerts can help you respond quickly to any IP-related issues.
6. Legal Recourse and Remedies
By understanding your legal options and being prepared to take decisive action in the event of an infringement, you can better protect IP security outsourcing.
If your Intellectual Property is misused or stolen, filing a lawsuit would help you seek compensation and stop the infringing activities. An injunction can prevent the offending party from using or disclosing your IP while the legal process is ongoing.
Consider alternative dispute resolution (ADR) methods like mediation or arbitration. These can often provide a quicker, more cost-effective way to resolve disputes without the need for prolonged court proceedings.
Steps to Take in Case of IP Infringement
Have a look at the key steps included in IP infringement:
1. Gathering Evidence
Collect all relevant documentation and evidence of the infringement. This can include emails, contracts, logs, and any other records that demonstrate how your IP was misused.
2. Working with Legal Counsel
Engage with legal tech experts who carry deep knowledge of intellectual property law. They understand your rights, evaluate the strength of your case, and guide you through the legal process.
3. Pursuing Enforcement Actions
Depending on the nature of the infringement, your legal counsel may advise you to pursue enforcement actions. This could involve sending cease-and-desist letters, negotiating settlements, or taking the case to court to seek damages and enforce your rights.
Also Read: Red Flags in Software Outsourcing: 7 Warning Signs You Can’t Ignore
Examples of successful IP protection in outsourcing
Implementing effective strategies for outsourcing IP protection can lead to successful outcomes. Here are a few case studies and examples that illustrate how companies have effectively protected their IP while outsourcing software development:
1. TechCorp
TechCorp, a leading technology firm, decided to outsource a significant portion of its software development to an offshore partner to accelerate time-to-market for a new product.
They crafted comprehensive contracts with stringent IP protection clauses, including non-disclosure agreements and clear ownership rights. They also implemented regular audits and monitoring to ensure adherence to IP protection protocols.
Outcome:
By employing these strategies, TechCorp successfully collaborated with the offshore partner without any IP breaches. The new product was launched on time, and TechCorp maintained full ownership and control of its IP.
2. PharmaSolutions
PharmaSolutions, a pharmaceutical company, outsourced the development of a proprietary software application for managing clinical trial data.
The company established secure communication channels and enforced data encryption for all sensitive information. They implemented continuous monitoring tools to track the usage and access of IP-related data.
Outcome:
PharmaSolutions successfully safeguarded its IP throughout the development process. The software application was developed efficiently, and the confidentiality of sensitive clinical trial data was maintained.
3. FinTech Innovators
FinTech Innovators, a financial technology startup, outsourced the development of a cutting-edge mobile banking app to gain a competitive edge in the market.
They established a robust legal framework with clear IP ownership and transfer provisions.
They further utilized advanced IP monitoring tools to ensure compliance and track the development process.
Outcome:
FinTech Innovators launched the mobile banking app successfully, with all IP rights outsourcing retained. The strategic approach to IP protection helped the startup secure its innovative solutions and enhance its market position.
Find out how to protect your IP when working with external partners.
Final Words
Outsourcing IP protection is a powerful tool for business growth and efficiency. However, it comes with unique challenges. By utilizing the above-discussed steps, you can navigate these complexities and safeguard your valuable assets.
Always remember that proactive measures are key to success. From thorough vetting to robust contracts and ongoing monitoring, taking time to build a secure foundation for your outsourcing partnerships will ensure your Intellectual Property remains protected.
Looking for a trusted software development partner?
At ValueCoders, we understand the importance of outsourcing IP protection. We help you hire developers for startups and avoid IP risks outsourcing. We take all necessary measures to ensure your organization won’t face any safety breaches.
Feel free to contact us today and learn more about how we can help you protect Intellectual Property when outsourcing!