As cyber threats evolve, so must our defense mechanisms.
Security isn’t just important, it’s essential in today’s digital world.
Application security is necessary to block attacks targeting your application. That’s the key idea behind a use-case driven approach, which is essential for fortifying your digital security.
By reading this blog, you’ll understand the complex issues around application security development through real-world examples.
In this blog, we’ll explain why security matters so much in software development. We’ll look at practical case studies and reveal the secrets to software product development life cycle.
Let’s not just build apps; let’s build them to be secure. Ready to learn more about coding securely?
Let’s get started!
Understanding the Landscape of Cyber Threats
It’s really important to understand cyber threats if you want to build secure applications. The internet is an amazing place for innovation, but it also allows hackers to take advantage of vulnerabilities.
Cyber threats are always changing and evolving. To make secure web apps, you need to wrap your head around these threats. Hackers use schemes like phishing or malware to attack systems, and the challenges keep piling up.
So, how do you actually make secure applications?
That becomes a key question as threats get more advanced. Building secure and scalable apps is necessary to avoid risks.
To take on custom software projects, you need to truly understand the software product development process. Cybersecurity in software development puts up an extra layer of protection against unseen threats in the code.
Uncover risks, secure code, and stay ahead of threats with our proactive security, shielding your applications.
The Role of Risk Assessment in Use-Case Security
Risk assessment is pivotal for protection against potential threats. Let’s understand the significance of this proactive measure in fortifying your digital fortress.
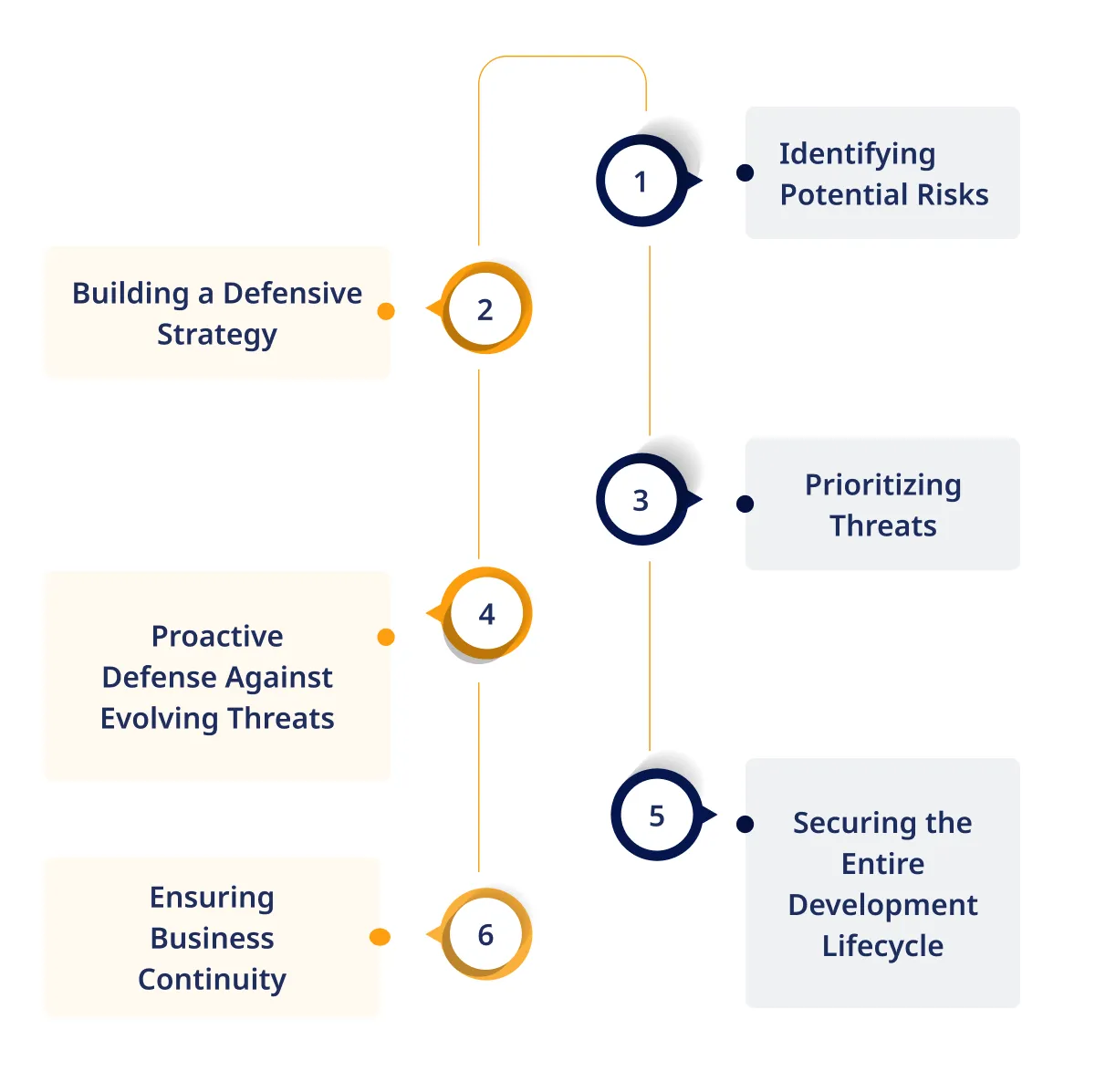
Identifying Potential Risks:
Risk assessment is the compass that guides you through the uncharted territories of potential vulnerabilities. It involves a meticulous exploration to identify, categorize, and understand the risks that could compromise the security of your application.
Building a Defensive Strategy:
Half the battle is won by knowing your enemy in application security development. Risk assessment serves as the foundation for creating a defensive strategy tailored to the unique use-case scenarios your application may encounter.
Prioritizing Threats:
Not all threats are equal. Risk assessment allows you to distinguish between potential threats, categorizing them based on severity and likelihood. This prioritization ensures resources are allocated efficiently to address the most critical risks.
Proactive Defense Against Evolving Threats:
The digital landscape and the threats it harbors are ever-changing. A use-case driven security approach, fortified by risk assessment, positions your defense proactively. Anticipating and preparing for potential risks becomes a continuous process rather than a reactive response.
Securing the Entire Development Lifecycle:
Building secure applications starts with securing every phase of development. Risk assessment isn’t a one-time event; it’s an ongoing process embedded in the entire lifecycle. Understanding and mitigating risks is ingrained in the development DNA from conceptualization to deployment.
Ensuring Business Continuity:
Beyond safeguarding your application, risk assessment contributes to business resilience. By identifying and addressing potential risks, you’re not just securing code; you’re ensuring the uninterrupted flow of business operations.
Risk assessment emerges as the compass that steers your course to a safer digital future when developing secure web applications and building secure and scalable applications.
As software developers, we build the digital infrastructure that runs the world. This comes with a responsibility to ensure security in software development.
If apps and systems have vulnerabilities, it leaves data and privacy at risk. So security needs to be a priority from day one of design, not an afterthought.
Also read: Cybersecurity In Software Development: Why It Matters More Than Ever
Key Components of a Use-Case-Driven Security Strategy
Developing a robust security strategy for secure application development involves meticulous planning and understanding of potential vulnerabilities.
Let’s understand the key components that form the bedrock of a use-case driven security approach.
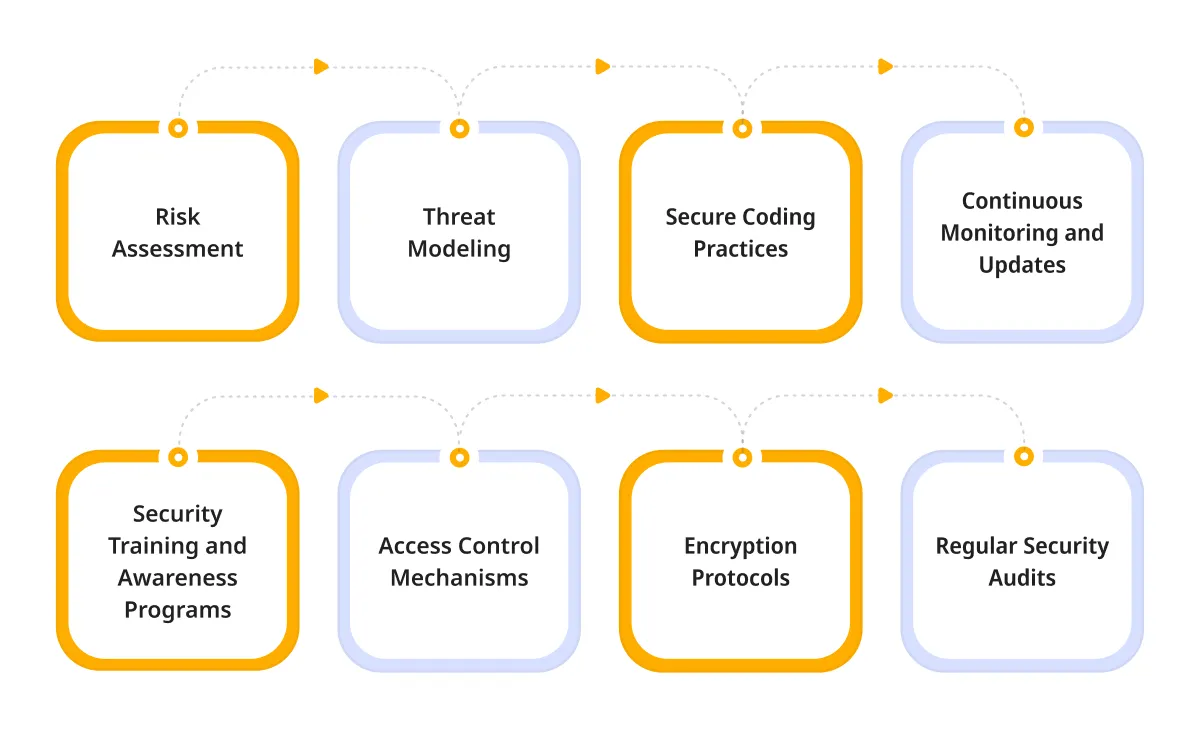
Risk Assessment:
Identifying potential risks is the cornerstone. Building secure applications starts with a comprehensive risk assessment. Recognize and prioritize potential threats based on use-case scenarios.
Threat Modeling:
Developing secure web applications necessitates anticipating potential threats. Threat modeling involves envisioning potential risks ensuring a proactive defense against evolving cyber threats.
Secure Coding Practices:
Building secure and scalable applications requires a codebase fortified against vulnerabilities. Secure coding practices involve adopting coding standards that mitigate common security risks.
Continuous Monitoring and Updates:
The journey doesn’t end at deployment in application security development. Continuous monitoring ensures real-time threat detection. Regular updates and patches are the shields against emerging vulnerabilities.
Security Training and Awareness Programs:
An often underestimated yet crucial component. Training and awareness programs ensure that every team member understands their role in maintaining security, from developers to stakeholders. Educating them on current threats and best practices creates a united front against potential risks.
We empower your development journey, making every line of code a fortress against cyber threats.
Access Control Mechanisms:
Implementing robust access control mechanisms is imperative. Define and enforce who has access to what parts of the application. This granular control minimizes the attack surface and prevents unauthorized access, contributing significantly to overall security.
Encryption Protocols:
Safeguarding data in transit and at rest is non-negotiable. Utilize industry-standard encryption protocols to ensure sensitive information remains confidential. This includes encrypting communication channels and employing secure storage practices.
Regular Security Audits:
Just as continuous monitoring is vital, periodic security audits add an extra layer of assurance. Regularly assess the security posture of your application through comprehensive audits, identifying and rectifying potential weaknesses before they become exploitable.
Incident Response Drills:
Practice makes perfect, especially in cybersecurity. Conducting regular incident response drills ensures your team is well-prepared to execute the incident response plan when a real threat emerges. This proactive approach enhances the effectiveness of your security strategy.
As a provider of software product development services, we emphasize integrating these components. Hire dedicated software development teams committed to implementing these strategies. Together, we fortify your digital presence against the ever-evolving landscape of cyber threats.
Stay tuned for more facets of secure application development in our journey towards a safer digital future.
Also read: Building Scalable Products: A Software Engineer’s Guide
ValueCoders Case Studies
Explore how ValueCoders has excelled in secure application development through the lens of our impactful case studies. Let’s examine the three projects showcasing our expertise in building secure and scalable applications.
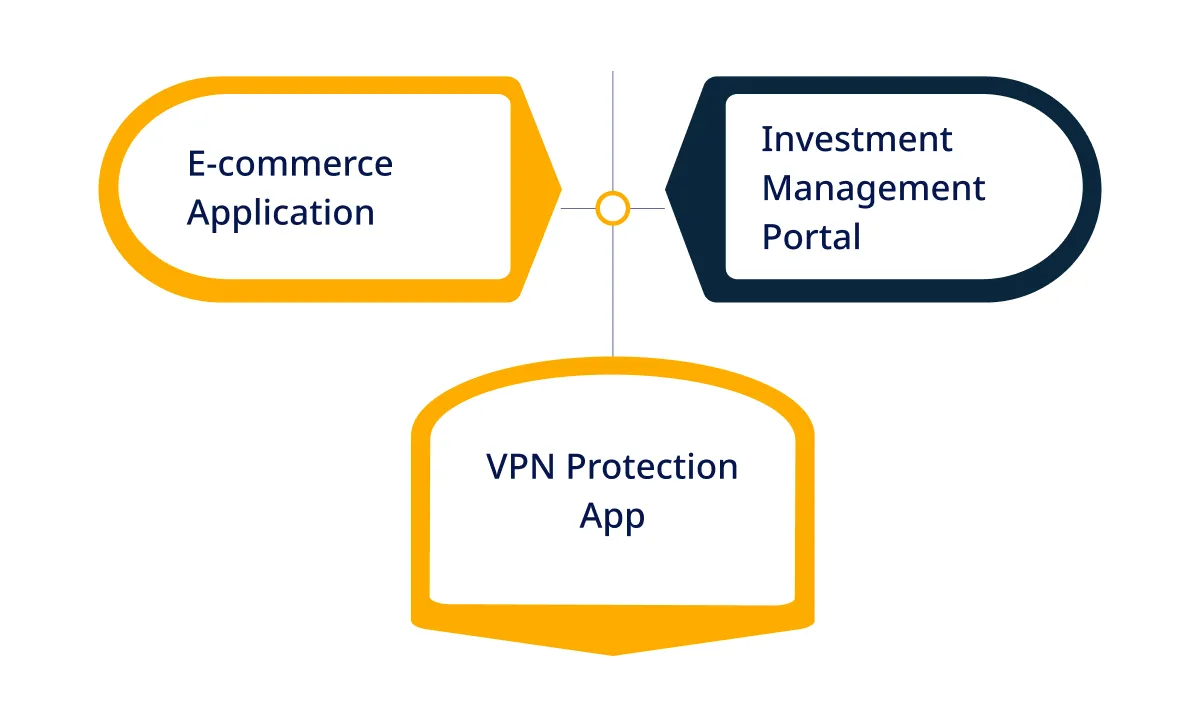
Learn about an E-commerce Application’s seamless integration for Android and iOS devices. Users enjoy direct interactions with sellers and secure transactions through a robust payment gateway and a responsive support system. Complete security is ensured, making the purchase experience safe and enjoyable.
Explore the Investment Management Portal developed by our experts that redefines financial interactions. The admin panel empowers with features like investing and trading plans, user role specifications, risk configurations, and strategy-building tools.
Admins can efficiently manage users, allocate teams, and ensure secure transactions, contributing to comprehensive application security development.
Experience the simplicity and effectiveness of our VPN Protection App. Developed for Android, it offers a minimalist interface ensuring privacy without the hassle of remembering passwords.
This app develops secure web applications, making internet communications private and secure. With a robust design, it minimizes vulnerabilities, making it a fortress against potential threats.
We bring these case studies to life at ValueCoders, a leading application development services company, demonstrating our commitment to excellence.
Our approach goes beyond, ensuring your app stands resilient in the face of cyber challenges.
Explore how our security testing and mobile app development services contribute to a safer and more efficient digital landscape. Join us on the journey of innovation and security.
Implementing a Use-Case Driven Security Framework
In secure application development, a robust security framework is not just necessary but a strategic imperative. Let’s understand the essentials of implementing a use-case driven security approach.
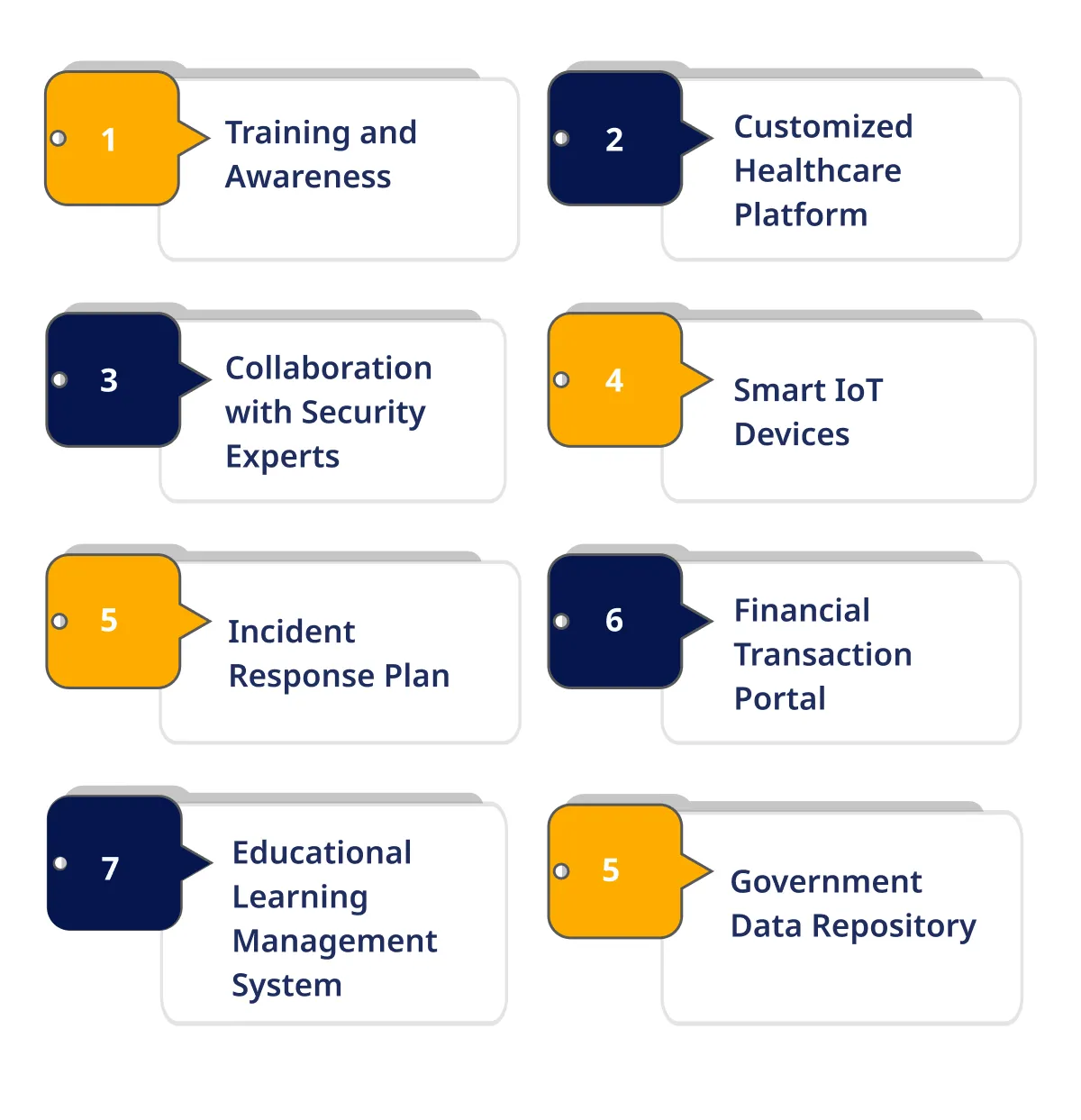
Training and Awareness:
Building a security-conscious culture is the cornerstone of this strategy. It’s not just about writing secure code; it’s about instilling a security mindset across your entire team. Training and awareness programs play an essential role in achieving this.
These programs involve educating everyone involved in the development process – from developers and testers to stakeholders. By imparting a deep understanding of the significance of security at every phase of development, individuals become proactive defenders against potential threats.
Collaboration with Security Experts:
In the complex world of cybersecurity, collaboration is vital. Bringing in security experts is akin to reinforcing your castle with the most robust materials.
Integrating these professionals into your development teams ensures that security considerations are embedded from the project’s inception. Their wealth of experience allows for identifying and mitigating potential threats early in the development cycle, preventing vulnerabilities from escalating.
Incident Response Plan:
Recognizing that no fortress is entirely impenetrable, having an incident response plan is like to having an emergency evacuation strategy. This plan is a meticulously created set of actions tailored to your specific use-case scenarios. It outlines the steps your team will take in a security breach.
This preparedness is crucial for minimizing damage and downtime, enabling your team to respond swiftly and effectively to contain and neutralize the threat. Implementing a robust incident response plan is crucial in today’s digital landscape. As part of maintaining comprehensive security, it’s essential to stay prepared for potential breaches. This includes integrating tools for effective incident response that can help identify and mitigate threats swiftly by conducting in-depth analysis and seamless collaboration with forensic capabilities, which are key components seen in many open-source security solutions. The incident response plan is not just a document; it’s a dynamic strategy that evolves with the evolving threat landscape.
Customized Healthcare Platform:
Imagine a healthcare platform where patient data is sacred. In this use case, a use-case-driven security framework involves rigorous risk assessment to identify potential data storage and transmission vulnerabilities.
Secure coding practices ensure that patient records are shielded from unauthorized access and that a well-defined incident response plan is in place to address any breaches swiftly.
Also read: Complete Guide To Software Development Services
Smart IoT Devices:
In a world of interconnected devices, a use-case driven security approach is crucial for smart IoT devices. Threat modeling becomes paramount to anticipate potential attacks on the network.
Continuous monitoring ensures these devices remain secure over time, with regular updates closing loopholes. Collaboration with security experts is essential to stay ahead of evolving threats in this dynamic landscape.
Financial Transaction Portal:
Handling financial transactions demands an airtight security framework. Risk assessment goes beyond the application layer to include the entire transaction process in this use case.
Secure coding practices are enforced to prevent fraudulent activities, and an incident response plan is finely tuned to minimize financial losses in case of a security breach.
Educational Learning Management System:
For an online learning platform, a use-case driven security framework focuses on safeguarding sensitive student data.
The security strategy includes training and awareness programs for educators and students, ensuring they understand the importance of secure practices.
Collaborating with security experts ensures the platform remains resilient against potential threats, fostering a safe learning environment.
Government Data Repository:
Securing government data is of utmost importance. A use-case driven security approach involves not only risk assessment but also compliance with stringent regulations.
Secure coding practices are applied to government applications, and continuous monitoring ensures that any unauthorized access or tampering is immediately detected.
Collaboration with security experts is essential for staying ahead of potential cyber threats targeting sensitive government information.
In each of these use cases, the use-case driven security framework becomes a tailored suit of armor, protecting the unique vulnerabilities and requirements of the specific application.
Our approach prepares your applications for conquest in the ever-evolving landscape of cyber threats.
As a reputable application development services company, we specialize in customizing these frameworks to suit the distinct needs of diverse industries, offering top-notch security testing services and skilled software developers to fortify digital solutions.
In Closing
When it comes to secure application development, adopting a use-case driven approach isn’t just a strategy; it’s a commitment to fortifying your digital realm.
As we navigate the complexities of application security development, a few truths emerge:
- Risk assessment becomes the guiding light, steering you away from potential vulnerabilities.
- Proactive defense isn’t a luxury; it’s necessary against ever-evolving cyber threats.
- Continuous monitoring and updates are the shields that guard your fortress in real-time.
- Collaboration with security experts and secure coding practices crafts an impenetrable defense.
In building secure and scalable applications, the destination isn’t just secure code—it’s business continuity, user trust, and a resilient digital future. Choose not just a service but a commitment to security. Take the next step with ValueCoders—your partner in securing digital excellence.
Get on the secure path. Your digital future deserves nothing less.